User Experience Comparison of Capturing Packet between Wireshark with nRF52832 Sniffer and Packet Sniffer with CC2540 Sniffer

In the Bluetooth development process, using a Sniffer to analyze the data received and transmitted by the Bluetooth module will undoubtedly greatly improve our R&D efficiency and help us quickly locate the problem. For beginners or developers, BLE packet capturing analysis allows us to understand the working process of Bluetooth more quickly.
There are several common Sniffers on the market. This article compares the user experience on Bluetooth capturing packet between Nordic nRF52840 Wireshark and TI CC2540 Packet Sniffer.
After testing, Wireshark's experience compared with Packet Sniffer's mainly includes three points:
1. Wireshark optimized software layout and simplified packet capturing process.
2. Wireshark parses the thorough packet structure captured to facilitate analysis.
3. Wireshark parses the packet type in advance for the captured data to facilitate finding the corresponding packet.
In the test, selected RF-Star's RF-DG-32A Sniffer based on nRF52832. Its performance and stability are better than TI's CC2540 Sniffer hardware. Engineers can try this RF-DG-32A.

Of course, the focus of this article is on the actual measurement comparison of software. Please see the following for the specific test analysis process.
First of all, we need to prepare the hardware and software before testing.
For the hardware part, we need to prepare RF-STAR's nRF52832-based RF-DG-32A Sniffer and tested modules: RF-BM-ND04 (nRF52832) module and RSBRS02ABR (RS02A1) module.
In the software part, we need to prepare the Android mobile APP: nRF Connect, which can be easily found and downloaded in the APP store. On PC, we need to download and install Wireshark.

After the above software and hardware are well prepared, we can start RF-DG-32A packet capture test.
First, we use the RF-BM-ND04 module for testing.
The specific steps are:
a. Plug the RF-DG-32A into the USB port of the computer, and then open "My Computer"-"Management"-"Device Manager"-"Port" to check the COM port number of the device.

b. Wireshark select the corresponding COM number, and double-click the COM number to enter.

c. Power on the RF-BM-ND04 module, open the corresponding software nRF Connect on the phone, check the MAC address of the device, you can see that the RF-BM-ND04 device address is FA:8D:0D:27:50:C6.

d. Click the "All advertising devices" selection box in the Wireshark, and select the device with MAC address FA:8D:0D:27:50:C6 in the drop-down selection box.
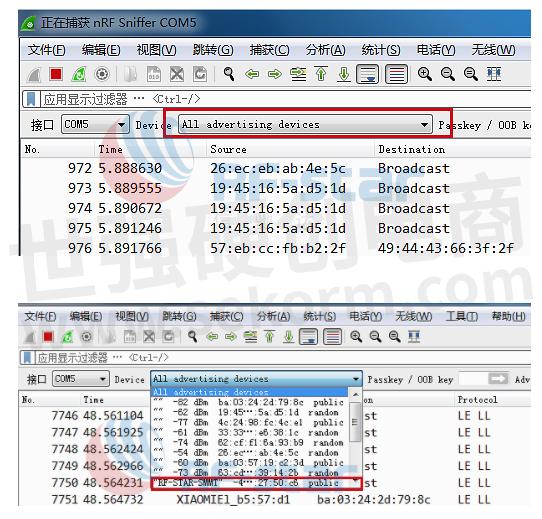
e. Click "CONNECT" on the mobile nRF Connect to connect to the Bluetooth module.
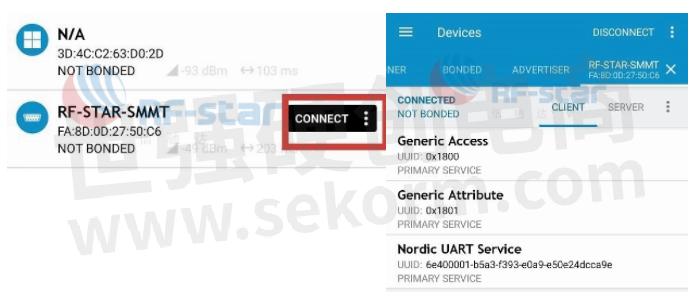
f. Select "Nordic UART Service" in the mobile nRF Connect, and send the data "rf-star" to the module in "TX"

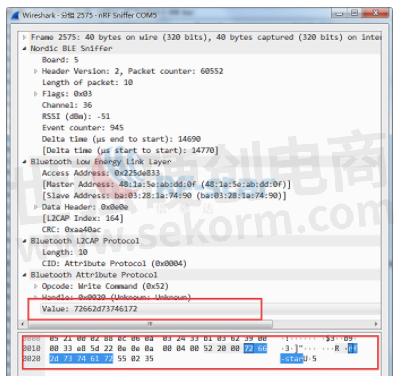
g. Before Wireshark sends data to the module, the data packets are displayed in the format of broadcast packet LE LL. Wireshark captures the correct data packet format as ATT. We only need to find the ATT format data packet and double-click ATT to view the data.
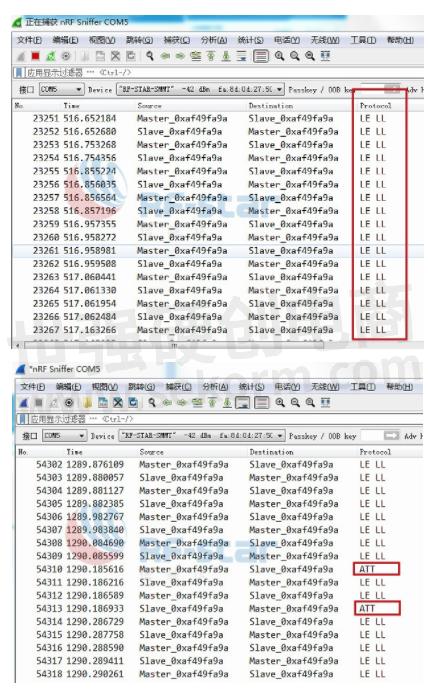
h. The interface of the data packet is as shown in the figure below, and the received data is parsed as rf-star, and the transmitting and receiving are consistent. The data has been successfully captured.

Let’s replace the transmitted data and repeat the above steps to test the sent data:
a. Repeat the above operation, the data transmitted by the mobile phone is modified to: https://www.szrfstar.com/. Wireshark capture results are:
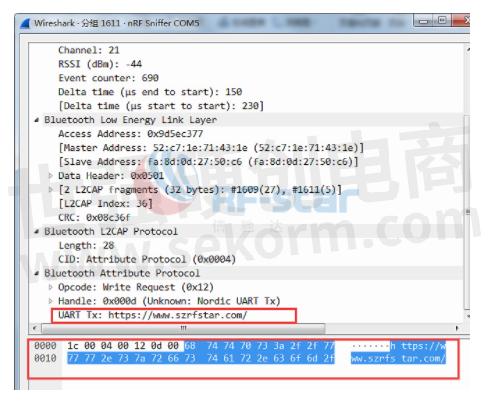
b. The mobile phone transmits the same data packet to the module multiple times: "rf-star". The data shown in the packet capture is as follows:

Remark:
When using Wireshark, you can pay attention to several tips. When you need to view the data, you can first click the stop capture button (red), and then observe the data. If you need to view the data, you can first click the stop capture button (red), and then observe the data. If you need to recapture, you need to click the restart current capture button (green). After clicking, you need to disconnect the device. Wireshark will automatically restart capturing packets, and then connect the device again to work normally. If Wireshark data is found to be stopped after connection, disconnect the device again and reconnect it to work normally
2. Then, we use the RSBRS02ABR module for testing.
The specific steps are:
a. Plug the RF-DG-32A into the USB port of the computer, and then open "My Computer"-"Management" - "Device Manager" - "Port" to check the COM port number of the device.

b. Wireshark select the corresponding COM number, and double-click the COM number to enter.

c. Power on the RSBRS02ABR module, open the corresponding software nRF Connect on the phone, check the MAC address of the device, you can see that the RSBRS02ABR device address is BA:03:28:1A:74:90.

d. Click the "All advertising devices" selection box in the Wireshark, and select the device with MAC address BA:03:28:1A:74:90 in the drop-down selection box.

e. Click "CONNECT" on the mobile nRF Connect to connect to the Bluetooth module.

f. Send the data "rf-star" to the module in the dropdown menu of ffe5-ffe9 in NRF connect. Before Wireshark sends data to the module, the data packets are displayed in the format of broadcast packet LE LL. Wireshark captures the correct data packet format as ATT. We only need to find the ATT format data packet and double-click ATT to view the data.

g. The interface of the data packet is as shown in the figure below, and the received data is parsed as rf-star, and the transmitting and receiving are consistent. The data has been successfully captured.
Let’s replace the transmitted data and repeat the above steps to test the sent data:
a. Repeat the above operation, the data transmitted by the mobile phone is modified to: https://www.szrfstar.com/. Wireshark capture results are:

b. The mobile phone transmits the same data packet to the module multiple times: "rf-star". The data shown in the packet capture is as follows:

3. After using RF-DG-32A to test packet capturing function with Wireshark, we use TI CC2540 Sniffer to test with Packet Sniffer.
Hardware preparation: CC2540 official USB dongle and RF-BM-04 module.

Android APP preparation: nRF Connect.
PC: Packet Sniffer.
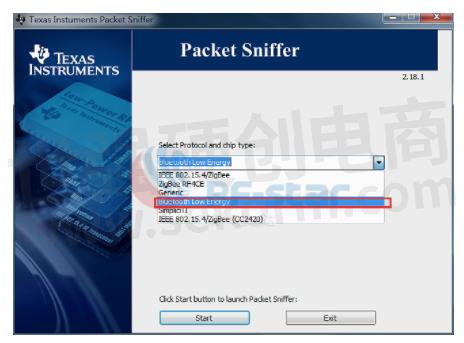
a. After installing the required software, open Packet Sniffer, select Bluetooth Low Energy in the interface, and click start below.
b. Click start and the interface is as follows, and the device will automatically identify the official USB dongle device

c. Click the Radio Configuration bar below, select the broadcast channel (37, 38, 39), and click the triangle start button above to search the broadcast information of nearby devices.

d. Open the mobile APP nRF Connect and check the address information of the device to be monitored as BA:03:28:1A:74:90.

e. Click the Display Filter column under the software, and select ADV_IND Adva in the Field Name.
f. Enter AA1=0x+ BA03281A7490 address in Filter Condition. Click first, AA1= will be automatically added, followed by the MAC address BA03281A7490, and click Add to add the device. Click Apply filter again to get the packet with the specified MAC address.

Through the above comparison test of Wireshark and Packet Sniffer, we can see that Wireshark's packet capturing experience is better than TI's Packet Sniffer.
First, Wireshark selects the corresponding COM port before entering the packet capturing, and Packet Sniffer selects the corresponding device through the bottom area. The design with large coverage in the bottom area makes the data display effect of the packet capturing process much worse than Wireshark. The style and layout of Packet Sniffer software are too old, and Wireshark is better than Packet Sniffer in software optimization.
Secondly, in the data displayed in Wireshark packet capturing, you can click the data to view the data structure in real time, and double-click to view the specific analysis of the lower layer protocol. Packet Sniffer can only display the split data structure and the specific values of some structures. In contrast, Wireshark can completely display the specific values of each structure of the received packets, which is called perfect parsing.
Thirdly, Packet Sniffer needs to check which message is the received data one by one, and needs some analysis methods to find the correct data. Wireshark has parsed every piece of data in advance, and can clearly know which one is LE LL and which one is ATT. the packets that need to be found can be found directly through the data marked ATT, which is very convenient and efficient. Moreover, the data can be sorted according to time and protocol, and can be found efficiently and clearly according to the actual data search requirements. After all, since Wireshark has been open-source, through the development optimization of a few thousand developers, the user experience has been well optimized, and the free and easy-to-use feature will attract more people to try.
RF-STAR has been focusing on Bluetooth for ten years and has rich experience in scheme design.RF-STAR is an industry-renowned and reputable provider of radio frequency solutions and low-power RF core devices.
- +1 Like
- Add to Favorites
Recommend
- RF-DG-32A USB Sniffer Based on NRF52832 Chip Launched by RF-STAR , Which Supports Major Wireless Standards
- RF-STAR RF-DG-40A Dongle——In-Depth Analysis of the Improvement of Nordic‘s Dongle Based on nRF52840
- RF-STAR’s New Modules Adopt NRF52833 Chip Will Come Soon
- RF-STAR Has Launched RF Modules Support Zigbee, BLE, Thread, and Other Multi-protocol Operations
- RF-STAR Launched The CC2640R2L Module With A Lower Cost And High Performance
- RF-STAR‘s Active Bluetooth IC Card Enables Gas Recharging at Home
- RF-star’s Development Kits of CC2340 BLE Modules Accelerate Projects
- RF-STAR Focused on the Bluetooth Field and Has Rich Experience in Solution Design
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.





























































































































































































































































































































































































































































































































































































































































































































































































































































































