Silicon Labs Wi-Fi 6 Solutions Help You Convince Buyers by Designing More Secure Wi-Fi Devices
Research: 72% of Smart Home Users are Concerned with Security – How to Convince Buyers with Better Wi-Fi Device Security?
The research firm Parks AsSoCiates reports that 72 percent of smart home product owners are concerned with the security of the personal data collected by their devices. Among all US internet households, nearly 50 percent have experienced at least one privacy or security issue in the past year. And 30 percent of those who don’t own or intend to buy Smart Home products say that the reason is… guess what, privacy and security concerns!
Lack of consumer trust is a significant barrier to full-scale Smart Home market take-off, and device manufacturers suffer the most – the slowed-down growth prevents them from cashing in their maximum revenue potential from the market.
Is There a Solution to Convince Buyers of Better Smart Home Device Security?
Yes, there is, and it starts with Wi-Fi, the most popular and fastest-growing wireless technology in homes worldwide. The sheer volume of Wi-Fi-connected Smart Home devices out in the market, such as cameras, video doorbells, sensors, lights, switches, and home appliances, make them highly exploited attack surfaces, jeopardizing product owners’ private data and property, and thus holding consumers back with their buying decisions.
Why are Wi-Fi Devices so Vulnerable?
One reason could be that many device manufacturers rely mostly upon standard Wi-Fi Protected Access (WPA, WPA2, WPA3) and Transport Layer Security (TLS). Unfortunately, these security features cannot protect the devices and users from all attack types. Logical attacks, including buffer overflow attacks and over-the-air (OTA) code injection attacks, account for more than 50% of all attack vectors, many of which are beyond the protection capabilities of the Wi-Fi protocol and transport layer security features.
Who Can Fix Smart Home Device Security?
If the solution lies beyond what the Wi-Fi and transport layer protocols can do, then the manufacturers of Wi-Fi devices are in the best position to fix the Smart Home device security. They can enhance the security capabilities of their devices to complement the protection provided by e.g., WPA and TLS. By safeguarding their devices with robust end-point security, manufacturers can differentiate themselves through trust, stand behind the value proposition of better privacy, and convince buyers at retail stores to make the next purchase decision in their favor.
How Can Silicon Labs Improve Wi-Fi Device Security?
How can Silicon Labs help device manufacturers convince Smart Home buyers of better privacy?
Silicon Labs is renowned as the technology leader in IoT security. Silicon Labs Wi-Fi System-on-Chip (SoC) solutions SiWx917 and SiWx915 comprises several crucial device security features that few other Wi-Fi vendor in IoT can offer in a single package, complementing the commonly used WPA and TLS.
The following sections explain Silicon LabsWi-Fi security solution for IoT devices:
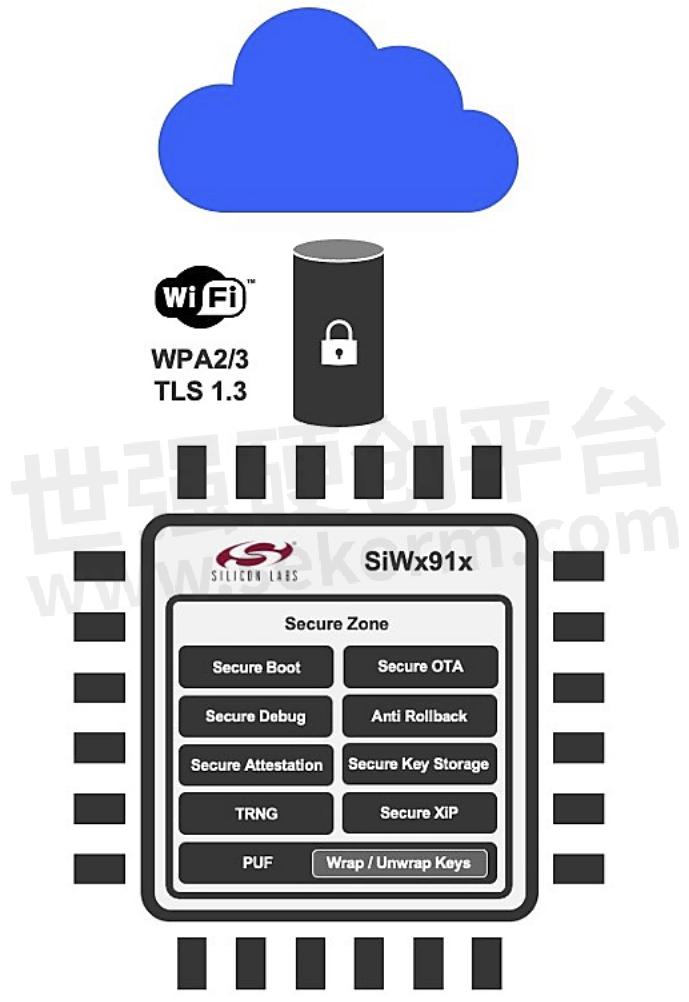
Secure Boot
Malicious code insertion is a common security threat for wirelessly connected devices, including Smart Home. Malware is inserted by a hacker to hijack the smart device to execute the wrong software in boot-up instead of the manufacturer’s authentic code. Silicon Labs SiWx917 and SiWx915 can help device makers eliminate malware insertion threats through its Secure Boot feature.
Secure Over-the-Air Update
Most Smart Home devices can have years of operational life. Software might have to be updated several times during this time. Each update represents a potential attack vector for hackers. Silicon Labs Wi-Fi 6 SoCs provide you with over-the-air (OTA) firmware updates, authenticating the source of the update file, encrypting the updating process, and guaranteeing an unaltered firmware image is used via the secure boot. Silicon Labs' secure OTA process can ensure your Wi-Fi devices always execute an authentic file during software updates.
Anti-Rollback
Rolling a device's firmware back to an older, vulnerable version is a potential attack vector, putting your installed base of Wi-Fi devices under threat. The Anti Rollback protection on Silicon Labs SiWx917 and SiWx915 prevents downgrading the device to an older version of its software, ensuring that earlier, potentially vulnerable versions cannot be used maliciously.
Secure Debug
Everyone familiar with programming knows that leaving the debug port unprotected can give hackers easy access to the internal computer architecture. The same applies to Wi-Fi Smart Home devices. SiWx917 and SiWx915 solve this with a secure debug mechanism – the debug port is locked by default and can be unlocked with an encrypted token to prevent unauthorized access to your Smart Home devices
Secure Zone
Secure Zone logically separates the memory into a secure processing environment (SPE) and a non-secure processing environment (NSPE). Only a predefined and restricted list of commands can be passed between these zones through an API, minimizing SPE exposure and securing the data stored there. On SiWx917 and SiWx915, Secure Zone prevents, e.g., external peripherals and Cortex-M4 application core from accessing the security processor, memory, and HW registers directly. It hides secret keys from the wireless stacks while safely providing the device maker with the same stack API. The cryptographic keys are stored in an encrypted way, improving the security of your Smart Home devices.
Secure Key Management
Hackers typically probe devices with various attempts to expose secret keys stored in flash memory. When a successful attack vector is found, it can be used to attack an entire installed base of similar devices. Secure key management is perhaps the number 1 challenge for wireless device makers. Silicon Labs’ Wi-Fi device security enables you to protect keys through the Physically Unclonable Function (PUF) and a True Random Number Generator (TRNG). The PUF key encrypts all keys in the secure key storage, and applications can handle the keys while remaining confidential. The PUF Key is generated at startup and is not stored in a flash.
True Random Number Generator
Random numbers are core to the security of any smart device, such as Smart Home. However, generating a truly random number is complicated. Hackers can use any bias in the numbers to reduce the effort and time to acquire keys. Pseudo Random Number Generators (PRNG) are prone to this vulnerability. SiWx917 and SiWx915 Wi-Fi SoCs use a True Random Number Generator (TRNG) that generates secret, high-entropy data based on RF noise, increasing the protection of your users.
Secure XIP
Silicon Labs’ SiWx917 and SiWx915 use Secure Execution in Place (XIP) to safely execute software directly from PSRAM, i.e., Flash memory, instead of copying it into RAM. To increase protection for the entire device, the software images are stored in an encrypted format and decrypted on the fly using the AES engine based on the PUF intrinsic keys specific to each device.
Conclusion: Convince Buyers by Designing More Secure Wi-Fi Devices
Global Smart Home revenue is expected to grow at an average rate (CAGR) of 11 percent in 2022-2028 and reach USD 232 billion at the end of the period*. However, as the Park Associates’ research found, most of the Smart Home product owners still don’t trust the security, and 30 percent of those on the fence with their buying decisions leave the products to the store for the same reason. This leads us back to the blog’s original question: How to convince Smart Home buyers with better Wi-Fi device security? Silicon Labs is here to help you with two highly secure Wi-Fi 6 solutions: SiWx917, which is an advanced ultra-low-power solution for battery-powered IoT devices, and SiWx915, which provides streamlined multiprotocol wireless and computing for line-powered devices!
- +1 Like
- Add to Favorites
Recommend
- Silicon Labs Ultra-low Power SiWx917 Wi-Fi 6 SoC: Ideal for Addressing Wi-Fi IoT Networking Challenges
- Silicon Labs’ SiWx917 Wi-Fi 6 SoC with Ultra-Low-Power Wi-Fi and AI/ML is a Match Made in the Cloud for AIoT
- Silicon Labs Simplifies IoT Development with Simplicity Studio 5
- Silicon Labs Strengthens Isolated Gate Driver Portfolio
- Software Speeds Development of IEEE 1588 System Integration | Silicon Labs
- Silicon Labs Expands Isolated Gate Driver Product Family Ideal for Hybrid and Electric Vehicles (EV)
- News | Silicon Labs and Amazon Collaborate on Sidewalk, a New Shared Network for IoT Consumer Devices
- Silicon Labs and Skyworks reach agreement to sell infrastructure and automotive business
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.

























































































































































































































































































































































































































































































































































































































































































































































































































