Securing Automotive Over-the-Air Software Updates




As the automotive industry moves toward full autonomy, the driver relinquishes more responsibilities to the vehicle. This increased scope of control raises the ceiling for software-related recalls as well as potential cyber-risk. As of 2022, software-related recalls issued by the US National Highway Traffic Safety Administration have increased by over 3x from 2009. Additionally, a 2022 Upstream report notes that over 50% of all existing automotive-related Common Vulnerability and Exposures (CVEs) were reported in 2021.
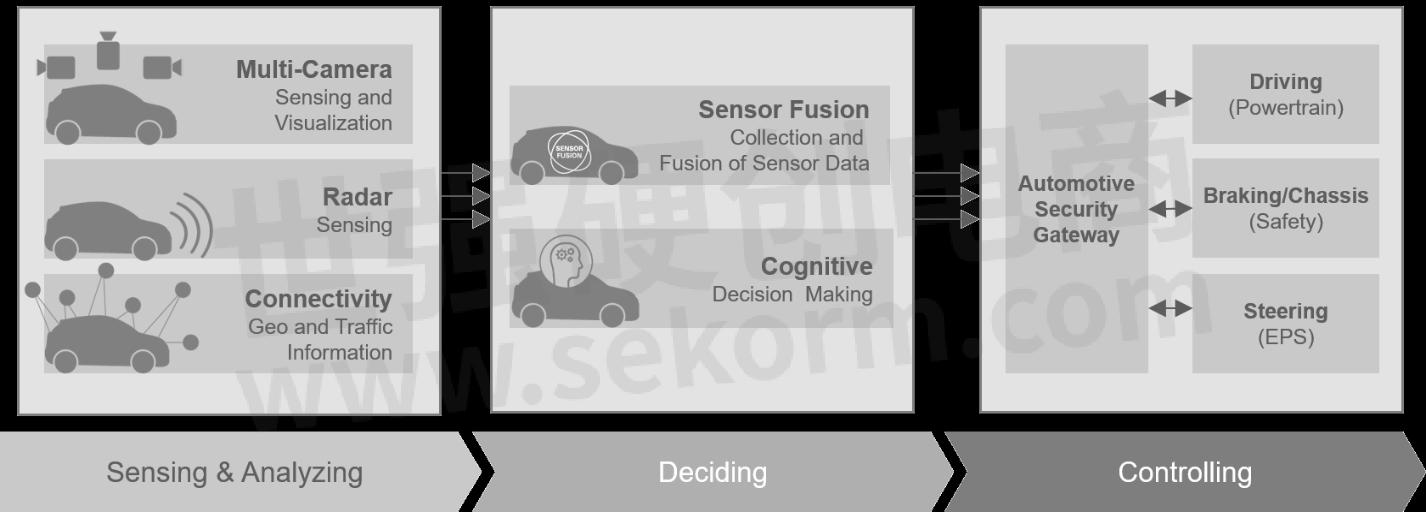
Figure 1: Modern Vehicle Architecture
It is no wonder software updates are an absolute necessity in automotive and, perhaps unsurprisingly, the automotive industry has used software updates in vehicles for many years. Until recently, software updates were generally reserved for development, vehicle manufacturing, or sometimes in a dealership service bay. Vehicles typically received few updates over their lifecycle. On the rare occasion, that a software update became available for a vehicle owner, it would typically require a trip to the dealership, or some manual process of updating with USB drives or CD-ROMs/DVDs. This results in an arduous rollout with low uptake. According to NHTSA, over 50% of all software recalls are not yet remedied. In short, the traditional way of doing updates is difficult, burdensome, and inefficient.
This problem space is the main driver of the new ISO24089 road vehicles standard for software updates engineering as well as the recent UNECE WP.29 R156 regulation on software updates and software management systems. UNECE R156 mandates software update management systems (SUMS) on all new vehicle types by July 2022 and in all new vehicles by 2024. Vehicle manufacturers must now, more than ever, focus on building safe and secure update systems.
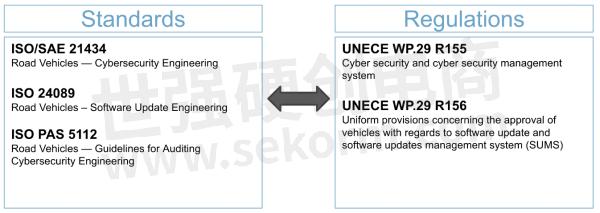
Figure 2: Software Update Related Standards and Regulations

Figure 3: Timeline for SUMS
In comes the saviour…
Software over-the-air (SOTA) allows manufacturers to quickly and remotely:
1. fix software issues,
2. respond to security vulnerabilities,
3. and extend or add functionality to a vehicle.
Software issues can be resolved without the need for expensive in-person recalls. Vehicles can be kept up to date with the latest security patches. OEMs (original equipment manufacturers) can add value after the initial sale or open new revenue streams from customers. Conveniently, OEMs can distribute software to an entire fleet at once or roll out updates in stages. All of this can be done from the comfort of an engineer’s ergonomically designed task chair.
Not so fast…the duplicitous nature of software updates
As you might imagine, this update-utopia isn’t entirely as it seems. There is danger hidden beneath the SOTA surface. The same mechanism that brings all these benefits, can also bring destruction. SOTA is by its very nature remote code execution. This tool in the wrong hands can make for a very bad day for an OEM.
Many examples of commercial update systems attacks exist; perhaps the most widely publicized is the SolarWinds exploit. In 2019, attackers compromised the IT management software company SolarWinds’ build system, staying undetected for months. They were able to sign malicious code into the build system to plant remote access tools into the software updates for Orion (SolarWinds’ IT management software). These updates containing malicious backdoors were unwittingly deployed to some 18,000 customers. Major organizations such as Cisco, Microsoft, Intel, and US Government agencies (including the Department of Defence and Department of Homeland Security) were affected. Because the attack was so pervasive and went on for months, the true extent of the damage may never fully be known.
Code signing and secure transport are not enough
The SolarWinds attack perfectly illustrates the problem with many software update systems. Because malicious actors may attack the update system itself, systems that rely on single-key code signing and transport layer security (TLS) may still be open to many types of attacks. Productions update systems must both understand that no system is compromise-proof and work to minimize impact when an attack does happen. By understanding the attacker's goals, designers can work to make systems resilient to attack.
Attackers of update systems intend to:
1. Read the contents of updates to discover confidential information, reverse-engineer firmware, or compare two firmware images to highlight changes between versions and perhaps identify vulnerable code sections.
2. Deny installation of updates to prevent vehicles from fixing software problems.
3. Disrupt functionality in the vehicle, denying use of the vehicle or of certain functions.
4. Control ECUs within the vehicle, and possibly the vehicle itself.
5. Modify the software to execute its own code.
An attacker with access to an update system or signing key may sign malicious updates or deny access to new fixes. If a malicious update is successfully installed in a vehicle, it may be difficult if not impossible to recover without replacing the affected ECU. Therefore, it is important to ensure updates are trusted before installing them.
Backend Security with Uptane
Thankfully, there are experts working to solve these problems. Uptane is a software update security framework specifically designed to meet the diverse needs of automotive software update management systems. Designed by a community of security researchers at NYU, SwRI, and UMTRI, as well as industry leaders in automotive security, Uptane is designed to reduce the effect of known attacks on software update systems, provide resilience against compromise, and minimize the damage if a system does become compromised. Renesas is an active participant in the Uptane standard, partnering with other industry leaders to elevate OTA security.
The Uptane framework takes a pragmatic approach, acknowledging that systems do and will get compromised. By using multiple layers of security and separation of roles, Uptane aims to eliminate single points of failure due to compromise. Uptane minimizes the damage an attacker can do if they obtain a signing key and provides mechanisms for remediation, helping resist against the highest degree of threat actors.
To provide this flexibility, Uptane uses two separate data repositories with different signing authorities. The image repository holds a database of all the signed images an OEM can deploy. Images are signed with offline keys which are themselves signed by a root signing authority. Offline keys are more difficult to compromise remotely because they require physical access and can support added security mechanisms like 2-factor authentication. The director repository takes advantage of the flexibility of online keys for machine-to-machine communication. The director will sign metadata for a particular update campaign instructing the vehicle to install a particular software bundle of software packages. This includes coordinating software updates with multiple ECUs.
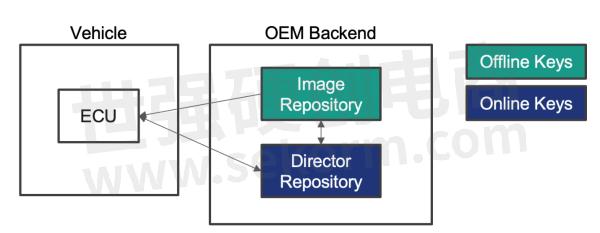
Figure 4: Uptane Repository Architecture
Splitting the repositories creates a separation of trust. This distributes responsibility so that the compromise of one key doesn’t affect the entire system. Additionally, threshold signatures are supported which can require a minimum number of signatures to attest to the authenticity of updates, again reducing the impact of a single key compromise. Revocation and updating of keys are an integral part of Uptane, providing a mechanism for replacing a compromised key. The most impactful keys, such as root keys and image signing keys, are designed to be offline. This minimizes the attack surface for the highest impact and most privileged keys.

Figure 5: Uptane Ecosystem
Renesas Device Security
Along with participation in the Uptane standard, Renesas is working to secure the entire end-to-end software update chain of trust. While Uptane allows an ECU to determine the authenticity and providence of software updates, several fundamental security attributes are needed including:
1.ECUs must have reasonable assurance that the updated software itself is trusted and unaltered
2.ECUs must have mechanisms to authenticate updates
3.ECUs must have mechanisms to securely store critical keys used in the update process
4.ECUs must have mechanisms to detect software tampering after an update is accepted
For these reasons, on-device security is imperative, and Renesas automotive devices supply the tools needed to increase security, lower the risk of compromise, and ensure software validity and authenticity.
After the software is validated and installed, it is up to the device to ensure the software is not tampered with after installation. This is where the secure boot is needed, and Renesas automotive devices support secure boot using dedicated security hardware, helping ensure ECU software stays trusted through the device lifecycle. Our recent blog series on secure boot in Renesas automotive devices goes into greater detail on these foundational concepts.
In addition to facilitating secure boot, the ICU-M (intelligent cryptographic unit master) hardware protected security environment in R-Car and RH850 MCU enables secure storage of cryptographic key material and other critical data. Secure key storage is essential to the security of the overall update system. A more in-depth breakdown of security features is found on our Renesas Secure – Automotive home page.
Renesas automotive devices also include dedicated hardware cryptographic accelerators. These can be used to accelerate secure communication such as TLS, as well as generate high entropy random numbers for nonces and challenge/response protocols.
Conclusion
As the industry pushes to implement the latest updates related to standards and regulations, we must ensure the continued safety and security of automotive vehicle systems. OTA is a double-edged sword. It is both a mechanism to facilitate a wealth of features and security updates and a significant attack vector for adversaries. Renesas actively contributes to the Uptane standard development and builds security enablement mechanisms directly into our automotive devices, increasing the resilience of update systems in the face of compromise. Renesas automotive devices incorporate security measures including:
1. Hardware-protected security environments for storing keys and running security firmware,
2. Secure boot to ensure the software is authentic and unmodified, and
3. Cryptographic accelerators for speeding up signature checks and secure communication.
Secure software update management systems combined with on-devices security ensure the best solution against attacks. Renesas continues to be a leading partner in secure software update innovation.
- +1 Like
- Add to Favorites
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.
Recommend
Using Example Projects to Support RA MCU Designs
2022-10-31 - Design Article With the extensive features and offerings supporting the RA MCU family and the Flexible Software Package, Example Projects can augment, simplify, and reduce the MCU design time.
The Need for Distributed Security Acceleration in Future Automotive Security Architectures
2021-01-01 - Design Article 4th generation RCAR devices are taking the first major step toward this goal, including domain-specific HSMs and parallel crypto-coprocessors, which can be assigned to assist specific virtual machines, application cores, or real-time cores in the SoC directly.
Cmsemicon‘s New BAT32A2 Series 32-bit MCU Complying with AEC-Q100 Standard Boosts Intelligent Automotive
2022-07-23 - New Product Introduction Cmsemicon has overcome the technical difficulties and recently released the new BAT32A2 series of automotive-grade MCUs with the AEC-Q100 Grade 1 automotive standard, now mainly used in automotive and high-end industrial markets.
Geehy’s G32A1445 Automotive General-Purpose MCU Certified by TÜV Rheinland for ISO 26262 ASIL-B
2024-05-31 - Product Introduction On May 16, 2024, Geehy’s G32A1445 automotive general-purpose MCU officially received the ISO 26262 ASIL-B functional safety certification from TÜV Rheinland.
What is the Difference between CPU and MCU?
2024-10-18 - Technical Discussion CPU (Central Processing Unit): The CPU is the core component of a computer system, responsible for executing instructions and processing data. It is typically used in systems with high performance requirements, such as personal computers, servers, and high-performance computing devices. MCU (Microcontroller Unit): An MCU is a single-chip system that integrates a processor core, memory, and peripherals, designed specifically for control applications. MCUs are commonly used in embedded systems such as home appliances, automotive electronics, and industrial control.
MindMotion‘s First Automotive MCU MM32A0144 Has Passed AEC-Q100 Automotive Certification
2023-06-10 - Manufacturer News MM32A0144 (MM32A0144C6PM), MindMotion‘s first automotive product series, has passed AEC-Q100 automotive-grade reliability test from a third-party authority. MM32A0144, featured with high performance, low power consumption and high reliability, can meet the needs of the automotive electronics industry.
Geehy APM32F003F6U7 MCU Receives AEC-Q100 Certification
2024-04-25 - Product Introduction Geehy‘s APM32F003F6U7 MCU stands out as a pinnacle of automotive excellence, certified with the stringent AEC-Q100 standard. In the automotive industry, where safety is paramount, this MCU ensures reliability and stability under challenging conditions, making it a trusted choice for electronic components.
WAYON Launches AEC-Q100 Automotive Grade 8-bit MCU – WY8A8503
2024-08-11 - Product Introduction WAYON WY8A8503 Automotive Grade 8-bit MCU adopts a TSSOP20 package form, supporting a wide voltage operating range of 2.5V to 5.5V. It has a main frequency of 16MHz, 16KB Flash, and 512B+256B RAM. It integrates two UARTs, one standard SPI, one standard I2C, and enhanced 6-channel PWM and 8-channel 12-bit ADC.
Automotive-grade MCU BAT32A237 from Cmsemicon Wins the 2023 Automotive Chip Top 50 Award
2024-01-19 - Product Introduction In the “Chip to E-Town” Automotive Chip Competition 2023, the Automotive-grade MCU BAT32A237 from Cmsemicon was recognized for its outstanding performance and awarded the 2023 Automotive Chip Top 50 in this automotive chip competition.
A New Member of Geehy Automotive-Grade MCU APM32F072RBT7 Certified AEC-Q100
2023-04-22 - New Product Introduction Recently, Geehy APM32F072RBT7 MCU underwent strict reliability tests by the third-party GRGTest and successfully certified AEC-Q100. This indicates that following APM32F103RCT7, the automotive-grade MCU chip team is expanding.
Cmsemicon Launches Automotive MCU BAT32A233, Further optimizing Analog Peripheral Resources
2024-01-21 - Product Introduction Cmsemicon announced the release of a new automotive MCU product – the BAT32A233. This product boasts the advantages of small resources, high performance, and support for the hardware LIN2.2 interface, making it highly suitable for compact and flexible parts in automotive applications.
Automotive LED Headlight Solution Based on APM32F103RCT7 Automotive-grade MCU to Improve Conversion Efficiency and Reduce System Cost
2023-06-10 - Application solution Article Certified AEC-Q100, the APM32F103RCT7 automotive LED headlight solution based on APM32F103RCT7 automotive-grade MCU supports CAN control, hard-wired control, and programmable configuration, helping engineers design multi-functional and high-performance LED drivers easily and quickly.
Six New Models of Cmsemicon MCU BAT32A2 Series Passed AEC-Q100 Automotive Certification
2023-09-29 - Product Introduction Cmsemicon announced that the automotive-grade MCU BAT32A2 series automotive certification is progressing well, and has passed the AEC-Q100 Grade 1 automotive grade reliability certification by the authoritative third-party testing and certification organization SGS.
Cmsemicon‘s 32-bit Automotive-Grade MCU BAT32A237 Wins the Automotive Market Breakthrough of 2023 Year Award
2024-01-18 - Product Introduction At the 2024 Semiconductor Investment Annual Meeting & IC Industry Award Ceremony, Cmsemicon has once again received good news, as its automotive-grade chip series BAT32A237 has been honored with the “Automotive Market Breakthrough of the Year Award“ for its advantageous market share and positive reviews.
CMSemicon‘s Automotive-Grade MCU BAT32A237 Passes AEC-Q100 Certification
2022-12-31 - Manufacturer News Recently, after five months of certification, CMSemicon‘s automotive grade MCU BAT32A237 series has passed the AEC-Q100 Grade 1 automotive-grade reliability certification by SGS, an authoritative third-party testing and certification organization.
Electronic Mall
Integrated Circuits
Discrete Components
Connectors & Structural Components
Assembly UnitModules & Accessories
Power Supplies & Power Modules
Electronic Materials
Instrumentation & Test Kit
Electrical Tools & Materials
Mechatronics
Processing & Customization











































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































