First Security Solutions for Renesas Automotive 16-bit MCU RL78 Make its Debut

Develop security functions efficiently with free sample software
Free sample software "AESEA Sample Security Driver" will be officially released in October 2022 to support software development of security functions for RL78/F23, and F24.
The sample software uses AESEA and TRNG circuits built into the Renesas in-vehicle 16-bit MCU RL78/F23, and RL78/F24 and performs encryption/decryption processing based on the AES encryption algorithm. The security function can be used simply by incorporating it into the user application software, which greatly reduces development efforts. It also supports Smart Configurator, a Renesas development tool.
* NDA is required to provide the "AESEA Sample Security Driver".

Figure 1. The software structure of AESEA Sample Security Driver
Main Functions:
AES ECB and CBC modes are processed by the hardware.
CMAC generation and verification of message data (Message authentication)
Detects tampering with user application programs stored in Code Flash. (Secure Boot)
Generates random number seeds, extends the seeds, and gets pseudo-random numbers.
Customers who want to incorporate the security of Evita-light without experience or development resources can use the software for the actuator applications in the latest E/E architecture where new control mechanisms and security considerations are required.
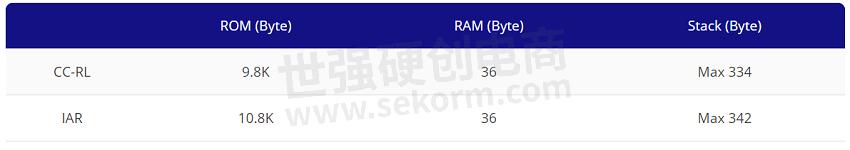
Table 1. ROM, RAM, Stack size of the AESEA Sample Security Driver
Following countermeasures against threats to the actuator area are also perfectly supported.
Table 2. Examples of Threats to the actuator domain and countermeasures
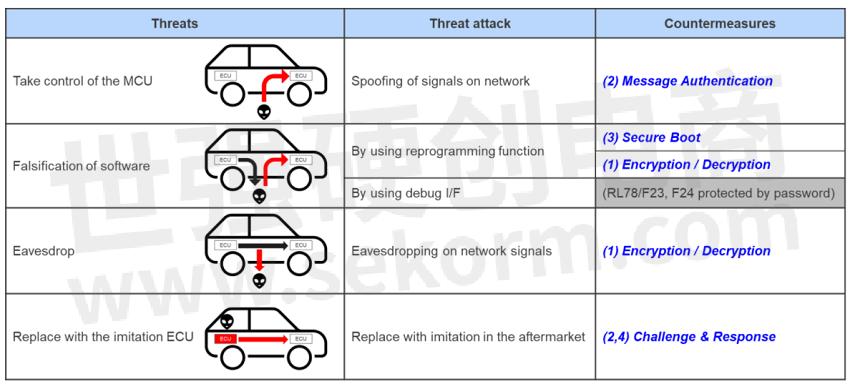
* For challenge and response, (4) is used to create challenge data, and (2) is used to create and confirm response data.
Following the AESEA Sample Security Driver, the security software libraries shown in Table 3 will be released in sequence. These are free security software that does not require an NDA contract and can be used not only with RL78/F23, and F24 but also with existing RL78/F13, F14, and F15. Security processing can be performed efficiently with an in-vehicle 16-bit microcomputer.
*Libraries for RL78/F13, and F14 will target products with 8KB or more RAM.
Table 3. Security software library

In the case of cryptographic algorithms that do not use a common key or secret key, the processing speed is slow, but the software is device-independent and has a high degree of freedom. If a coprocessor or the like is installed in a product and a vulnerability is found, it will cost a huge amount of effort to fix it.
Remarks: Free sample software has no warranty and no support.
Easy to start security with Renesas Solution Starter Kit for RL78/F23, F24
A Renesas Solution Starter Kit (RSSK) bundled with the free sample software (AESEA Sample Security Driver) introduced in Part.1 will be built. It enables software development of security functions while checking the actual operation and results on the actual board and GUI software.

Figure 2. RL78/F24 Security RSSK Development Schedule
Security RSSK ver.1 is planned to be released in early 2023 at first. It allows encryption/decryption and key registration using RL78/F24 target board and terminal software only for users who have signed NDA.
Figure 3 shows an image of Security RSSK ver.1. Connecting the serial data transmission (TxD) / reception (RxD) of RL78/F24 to the PC with a serial USB conversion cable, etc., and using terminal software on the PC to support software development of security functions.
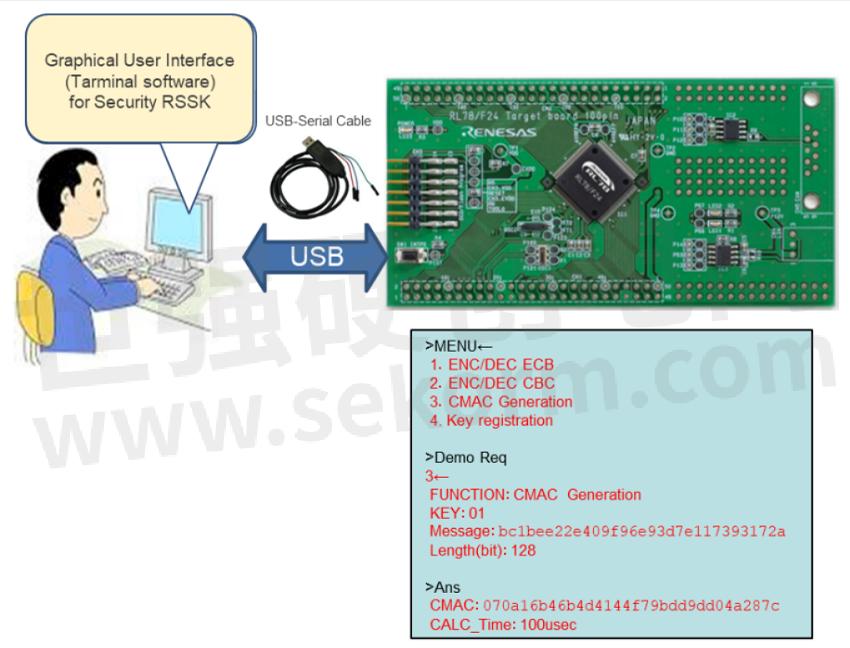
Figure 3. Image of software development using Security RSSK ver.1
Security RSSK ver.2 will be released around October 2023 as the second step. It is a set of dedicated security boards and GUI. Security RSSK ver.2 enables security functions such as encryption/decryption, secure boot, key registration, random number generation, and challenge & response to be executed with GUI operations. Beginners of security applications can use it to study security functions. Therefore, users who have not signed an NDA will be able to use it with some functional restrictions (for example, usage of challenge and response for authentication function).
Figure 4 shows the block diagram of Security RSSK ver.2. CAN-FD/CAN, debug, and USB interfaces, as well as output/display LED, LCD, and speaker are prepared. Flash memory is used for reprogramming and as a user program storage area if an NDA is not signed.

Figure 4. Block diagram of Security RSSK ver2
Table 4 shows the main functional differences between with and without an NDA. Note that functional restrictions can be removed after signing an NDA.
Table 4. Functional differences with and without an NDA
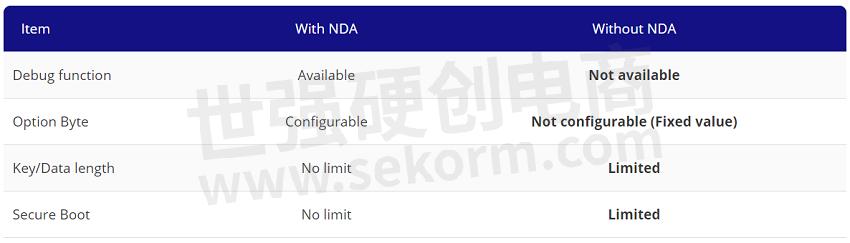
Figure 5 shows the GUI image of the key calculation tool based on SHE, which is one of the GUI images of Security RSSK ver.2. Current key storage status can also be displayed in the GUI.
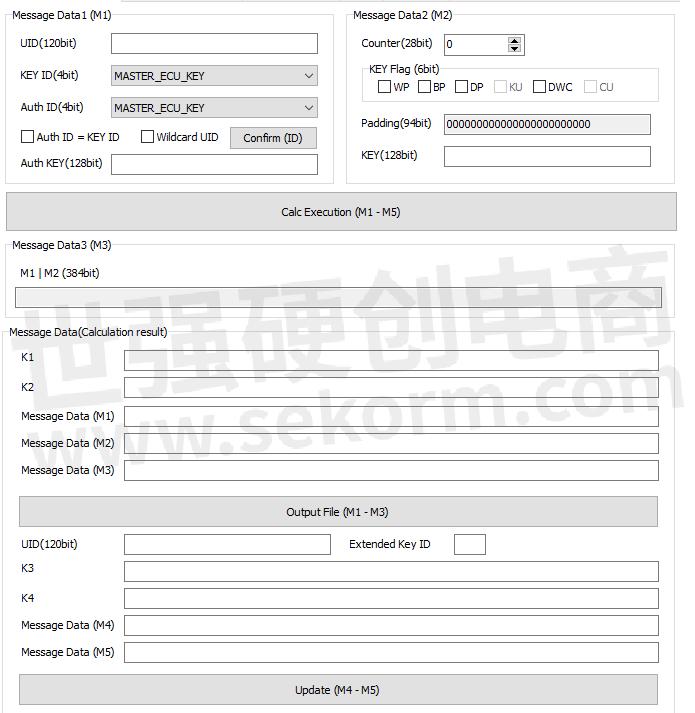
Figure 5. GUI image of key calculation tool based on SHE
The development of Security RSSK is ongoing. The content and schedule are subject to change as it is still in the planning stage. We hope that it can be adapted to various needs, such as those who want to develop software efficiently even with limited security knowledge and/or resources, or who just want to use security functions or just for study.
- +1 Like
- Add to Favorites
Recommend
- A Renesas Success Story in Vehicle Control Applications with RL78/F1x MCU Series
- Renesas Introduces Low-Power RL78/G15 MCU with the Smallest 8-pin Package Option Available within the RL78 Family
- Renesas Announced 16-bit RL78/G24 MCU Delivers Top-Class Performance for Motor Control and Power Supply Control Systems
- RL78/G15 MCU, a New Release of the Renesas RL78 Family Products,Solves the Existing Issues Faced by Many 8-bit Users
- Renesas‘ MCU RL78/G23 achieves world‘s highest EEMBC ULPMark™-PP score!
- Renesas Smallest 16MHz Touch Microcontroller RL78/G16 for 8-Bit MCU Market
- Release of 12V Motor Control Renesas Solution Starter Kit for RL78/F24
- Renesas RL78/G24 16-bit MCU Delivers Performance Comparable to 32-bit MCUs, with a FAA and CPU Operation up to 48MHz
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.






























































































































































































































































































































































































































































































































































































































































































































































































































































































