Renesas Secure Key Installation with Free of Charge DLM Service

The increasing growth of connected devices drives the need for secure communications and secure storage. OEMs must evolve the application capability whilst keeping compatibility with legacy and existing solutions. Especially the handling of cryptographic key material is a significant challenge even at the production stage.
A secure element might seem an ideal solution; by design, it provides a very high level of physical tamper resistance (even though most applications would not demand it) and is a self-contained, isolated, and separate subsystem. But it has major weak points, though. Besides the increased cost, it is low bandwidth and a single-point-of-failure connection. The secure key storage is quite limited. The performance of the crypto accelerators is typically not documented (see references section for an independent benchmarking), few algorithms might not be supported at all, and/or not upgradeable in the field. Additional key handling tools must be integrated into the production flow or a secure programming service employed at additional cost.
The Renesas Secure Crypto Engine (depicted in Figure 1) provides functionality comparable to a secure element with important benefits: a much higher performance, reduction of a bill of materials cost, and simpler integration of the necessary crypto functionality. It supports all state-of-the-art algorithms and a true random number generator. It enables secure and virtually unlimited key storage. The SCE subsystem is fully isolated and contained within the MCU, protected by an access management circuitry that shuts down the interface when detecting illegal access attempts. All plaintext crypto operations use dedicated internal memory, and the advanced key management capabilities avoid exposure on the internal bus fabric.

Figure 1. Secure Crypto Engine
But how to secure the factory key provisioning operations, without using a hardware security module (HSM)? All Renesas MCUs have historically supported factory programming over serial and USB interfaces, as a very reliable and low-cost mechanism suitable for mass production. The same interface can now support application key material injection.
Users can pass a chosen “installation key” and an encrypted payload (the “application key” be injected) to the SCE boundary via the built-in boot firmware, according to a documented protocol. A conceptual diagram is shown in Figure 2 below:
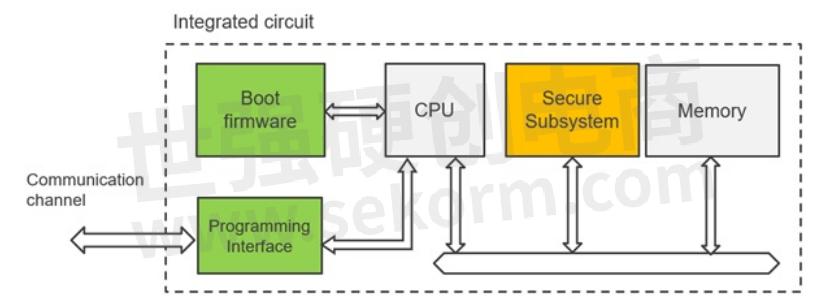
Figure 2. MCU provisioning over the programming interface
The SCE includes a Hardware Root Key (HRK), protected and unaccessible outside of its boundary. Key derivation functions are implemented to derive "key encryption keys"(KEKs, or HRK') which can transport any user key (in encrypted format) securely inside the SCE boundary for further processing. The preparation of the application key for injection is shown in Figure 3.

Figure 3. DLM server and key installation
In the first step the user chooses (generates) an AES install key (in green), and the desired application key (in yellow). The application key can be any type or size supported by the SCE engine, symmetric or asymmetric. Note: this preparation shall be done in a secure environment to preserve key confidentiality.
The application key is encrypted by the install key. Obviously, the install key shall be encrypted as well, to avoid easy interception and breach of confidentiality; and to achieve that, the HRK must be made accessible to the user. To encrypt the install key with the HRK - without exposing the HRK itself - Renesas provides a free-of-charge service to its customers. This service is delivered by a dedicated secure server (DLM server) designed to assist the MCU Device Lifecycle Management, in handling crypto keys during production and (optionally) later field updates. Any user can register free of charge to use the service, and generate the necessary data for the factory programming operation. All the communication between the user and the server is secured and encrypted via PGP.
In Figure 3, the green key 'embedded' within the blue key represents the HRK encrypted version of the user install key, which gets returned back by the DLM server. Please note that the application key (yellow) is never disclosed!
The encrypted install key can now be handled over to the SCE for decryption, and in turn, this gets used to decrypt the user key. At this point, the yellow key has been securely transported and reconstructed within the SCE boundary; now it must be saved in the MCU memory, otherwise, when power is removed, it will be lost.
To implement secure storage, the SCE implementation has another ace up its sleeve: the Hardware Unique Key (HUK). The HUK is a read-only, 256-Bit key exclusively accessible by the SCE access management circuit through a dedicated (private) bus. As for the HRK, KDFs can combine the HUK with API key generation information, and the derived keys can be used for implementing key wrapping i.e., secure key storage. The HUK itself is also stored in wrapped form in an isolated memory area (therefore, well protected from illicit access, copying, and tampering). The resulting wrapped keys can then be safely exported from the SCE boundary to be saved in non-volatile memory.
Noticeably, the installation key has no practical value outside of the factory and does not need to be stored; preparation of the installation key bundle can be performed completely "offline", and does not need an active network connection on the production site. Also, the SCE drivers provide additional APIs to use factory-installed keys for performing a "key refresh" (or key injection) in the field.
Consequently, the end application has no dependency on the DLM services during factory programming or while in the field.
This solution provides many advantages to the end user.
* Unlimited key storage, any program or data flash area available in the MCUs can be used.
* The HUK uniqueness prevents illicit cloning and copying of keys to another device.
* No need to implement a secure area on the factory floor, all keys are encrypted.
* The application keys never leave the customer's secure environment.
* No need for 'online' communication between the factory programmer and the DLM server.
* Program application and keys on the same interface, simplifying the flow.
In summary, Renesas provides a cost-effective and easy-to-use solution to help customers migrate to higher security levels in their applications. This functionality is available on the Cortex-M33-based microcontrollers of the RA6 and RA4 series.
References:
[1] Evaluation Kit for RA6M4 MCU Group
[2] R01AN5562EJ0100 Standard Boot Firmware for the RA family MCUs Based on Arm® Cortex®-M33
[3] R01UH0890EJ0110 RA6M4 Group User’s Manual: Hardware
[4] Renesas Flash Programmer (Programming GUI)
[5] Renesas Flash Programmer user manual
[6] Renesas RA Family Device Lifecycle Management Key Installation
[7] Quantitative comparison between external and internal acceleration solutions
- +1 Like
- Add to Favorites
Recommend
- Renesas RA6 Series MCU Innovation Kits for Connected IoT Applications
- Renesas DSP Solution on Renesas Lab on the Cloud, Input Analog Signals Directly From A Signal Generator To The Rx231 Microcontroller Evaluation Board
- Renesas‘ Semiconductor Manufacturing Factory (Naka Factory) Fire: Production Capacity Has Recovered to 88%
- Renesas Announces 10 New Winning Combinations Integrating Celeno and Renesas Products
- Renesas & Altran to Deploy First Social Distancing Wristwatch Using Ultra-Wideband Chipset with Low Rate Pulse
- Renesas and FAW Establish Joint Laboratory to Accelerate Development of Next-Generation Smart Vehicles
- Renesas Semiconductor Manufacturing Factory (Naka Factory)‘ Production Level Has Returned to 100%
- Renesas and Sequans Expand Their 5G Collaboration including Broadband IoT Module for 5G NR FR1/FR2
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.





























































































































































































































































































































































































































































































































































































































































































































































































































































































