Microsoft Exchange Server EWS Insecure Deserialization, Leverage Subscription Service to Stay Ahead of Attacks

With the recent events, there have been speculations regarding increasing cybersecurity attacks on organizations by the threat actors. Amidst the speculations, name of a CVE which has popped up is CVE-2020-17144 which is a Remote Code Execution (RCE) vulnerability in Microsoft Exchange Server 2010 SP3.
What is Microsoft Exchange
Microsoft Exchange is a mail and calendaring server implemented using ASP.NET. Microsoft Exchange Server provides web access for Exchange Web Services (EWS) which is an application program interface (API) that allows programmers to access Microsoft Exchange items such as calendars, contacts, and email.
Vulnerability Details
This CVE affects all the versions of Microsoft Exchange 2010 SP3 till Cumulative Update (CU) 30 (released on 08.12.2020). There is a Proof of Concept (PoC) publicly available on Github. We will test out the PoC on a test machine in a moment. Before we do that, here is a brief, simplified explanation of the root cause of the vulnerability - EWS uses SOAP (Simple Object Access Protocol) messages, which are XML based to access and modify the user configuration object. One of the methods (CreateUserConfiguration) accepting SOAP messages has a field called "binary data" which accepts serialized data. This serialized data is de-serialized on the server side without any validation. So, an authenticated attacker can embed malicious data in these SOAP messages capable of performing RCE causing the vulnerability.
Attack in action
1. Configuring the target
Firstly, we need a Windows OS which supports deployment of Microsoft Exchange Server. For that we deploy a Windows Server 2012 VM. We can get one evaluation ISO from here.
We will use the same VM to launch the attack too. We can use some other machine on the same network as well.
Active Directory (AD) Domain needs to be deployed on this machine. We can follow the guide from one of my previous blogs in the 'Deploying the Domain Controller' section.
After deploying an AD, we need to install the Microsoft Exchange Server 2010 SP3.
The version downloaded won't have any Cumulative Update installed. Visual Studio C++13 is needed if we want to apply the latest vulnerable Cumulative Update 30 over it.
Next, we need to the deploy the MS Exchange server 2010, we can follow the tutorial here.
Once the Exchange setup done, we need to make sure we can login to the following URLs by visiting them in the browser - https://localhost/owa and https://localhost/EWS/exchnage.asmx
Optional: We can disable SSL for EWS to see what's being exchanged in the wire in plain text. To monitor we need to download a network monitoring tool like Wireshark.
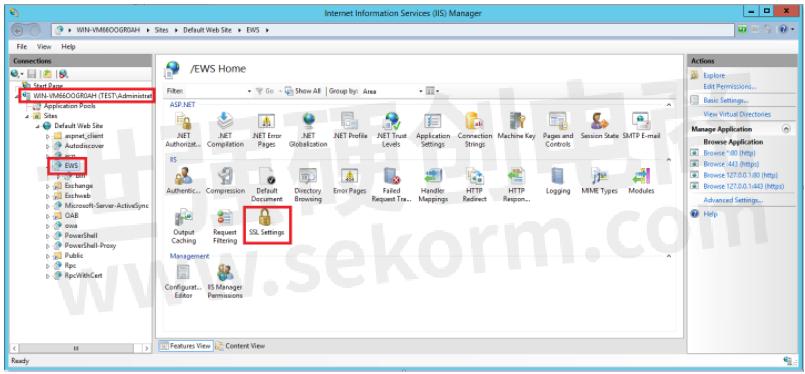
To disable SSL, search for IIS manager and go to the SSL settings of EWS and remove the check on the Require SSL option.
2. Preparing the payload
We download the Public PoC available online and navigate to it inside Command Prompt.
The payload needs to be compiled, but before compiling, if SSL has been disabled for EWS, open the CVE-2020-17144.cs file in a text editor and replace the word https to http.
Now in command prompt, run the batch script called make. This should create the CVE-2020-17144 file which is our payload.
3. Executing the Payload
To give an idea of what the payload is designed to do is, it creates a serialized object, which hosts a malicious server/webpage on the server, which can respond to user query by executing the commands that is supplied, whoami in this case.
Now, to launch the attack, run -
CVE-2020-17144 <ip_address> <username> <password>
Replace the IP address, username, and password with corresponding details
This should return successfully with message 'User Configuration Created', which means the attack probably has been successful.
To test if the attack was successful -
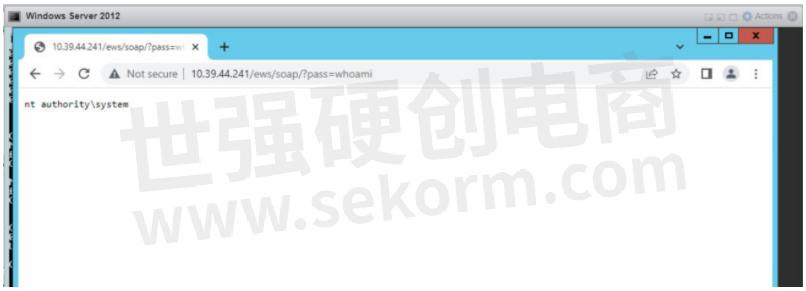
Visit http://10.39.44.241/ews/soap/?pass=whoami in the browser
This should return the username which means command execution was successful
We have also tested it to be working on Exchange Server 2010 SP3 with Cumulative Update 30.
Traffic on the Wire
While we executed the payload, we used Wireshark to monitor the packets exchanged over the network.
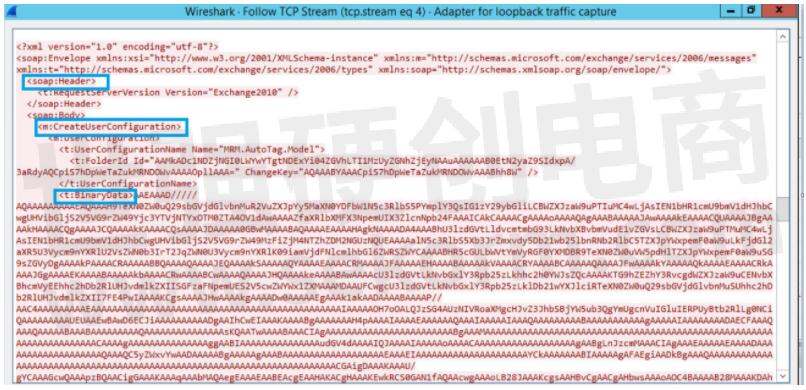
We notice a few things that we discussed while talking about the reason of the vulnerability to be true here.
We see the payload being delivered using SOAP messages.
We see the XML tag CreateUserConfiguration indicating the usage of vulnerable function.
We also see the XML tag binary data containing the malicious serialized payload Base64 encoded.
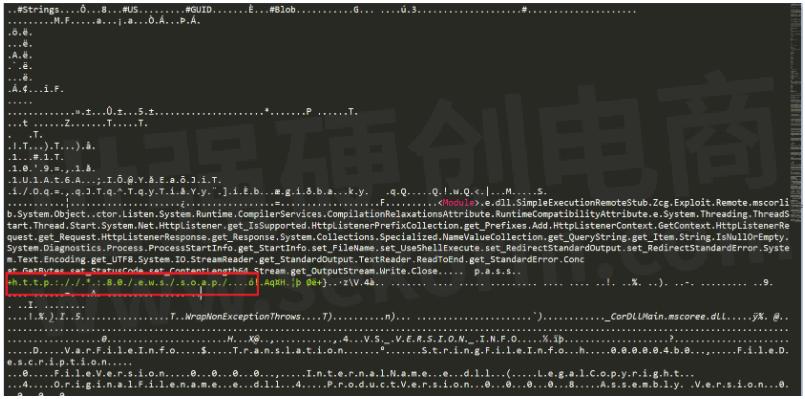
If we base64 decode the payload, we can see some info like the URL where the payload will start the server, which we used to verify the attack has worked.
Mitigation
To be able to mitigate this attack, make sure to apply the latest Cumulative Updates, at least CU 31 to the vulnerable Microsoft Exchange 2010 server.
You can also use Keysight test platforms with ATI subscription to be able to safeguard your network against such attacks. Keysight Threat Simulator or BreakingPoint products can help you assess your network security controls and determine whether you can be protected prior to patch. This kind of assessment is valuable as it can let you know if you have protection during the time before a change management window will open.
Leverage subscription service to stay ahead of attacks
Keysight's Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Keysight test platforms. The ATI Research Center continuously monitors threats as they appear in the wild and has just released a strike for this CVE as part of BreakingPoint System's recent update 2022-05.
The following image shows a screenshot of this CVE as a strike in BreakingPoint System.
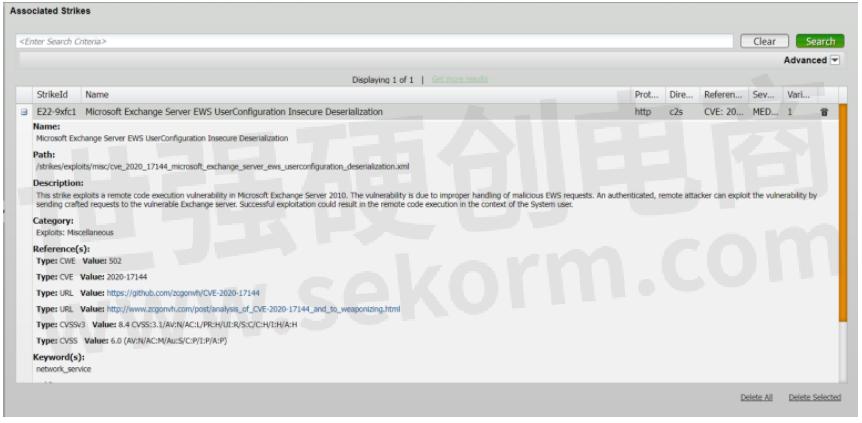
Customers of BreakingPoint now have access to attack campaigns for different advanced persistent threats, allowing them to test their currently deployed security controls' ability to detect or block such attacks.
- +1 Like
- Add to Favorites
Recommend
- Keysight‘s Take on CVE-2022-30190 MSDT Follina Exploit
- Keysight Technologies Acquires Quantum Benchmar, Augmenting Keysight‘s Quantum Portfolio
- Keysight‘s Take on Spring4Shell
- Keysight First to Gain OmniAir Qualified Test Equipment Status, Accelerating C-V2X Device Certification
- Keysight First to Gain GCF Approval of Cases for Validating 5G New Radio mmWave Devices in Standalone Mode
- Keysight Massively Parallel Board Test System Selected by LACROIX in Automotive Printed Circuit Board Manufacturing
- Keysight, TIM and JMA Wireless Join Forces to Showcase O-RAN Technology at Mobile World Congress 2021
- Keysight, Xilinx and Cisco Showcase Solutions that Support Smooth Migration from 4G LTE Networks to 5G Open RAN
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.












































































































































































































































































































































































































































































































































































































































































































































































































































