Bluetooth Security® – How to Build Next-Generation Secure Key Management
2021 Bluetooth® Market Update suggests that Bluetooth Low Energy is growing significantly in the industrial, commercial, home, and wireless medical IoT segments and is quickly becoming a favorite attack target for these digital pirates. Bluetooth beacons are used in the medical industry to track high-value assets like glucose meters. Hacking into such devices allows cybercriminals to control the sensor and read patient data. They can then relay the readings to their building management systems. Phones have also become a universal digital key to several devices like door locks and access control systems. Hacking into such systems gives cyber pirates access to critical digital information or physical assets. Hackers can break into these systems by getting access to the security keys used by the Bluetooth protocol to secure the communication link.
Bluetooth Security and Keys
Security keys are a large string of characters and numbers. They are used in security algorithms to encrypt and decrypt information. Bluetooth devices generate and exchange several security keys during the initial pairing process. Devices do this to identify each other and create a secure link for future communication. These include several ephemeral or temporary keys such as the device’s public keys, the elliptical curve Diffie-Helman (ECDH) keys, the MAC (Message Authentication Code), and many more keys. However, these keys are only relevant during the pairing process and can be discarded once the process is complete.
The pairing process also generates persistent keys like the Identity Resolving Keys (IRKs), which are used to resolve private addresses, and Long-Term Keys (LTKs), which are used to create session keys and encrypt the messages at the link layer. These persistent keys are the ones that require secure storage, and the Bluetooth Specifications leave the storage of keys to the discretion of the Bluetooth Low Energy device manufacturers. Semiconductor players like Silicon Labs can help address this requirement of secure key storage through innovative technology.
Back in the day, pirates would bury their treasures in faraway lands and hide the keys in the scruff of their beards. With the obvious problem of running short of beard space, physically storing the keys is no longer a viable option. In the semiconductor world, security keys are stored in key storage and management devices. However, these storages are like a vault that needs a key to ensure secure storage of the Bluetooth keys. This brings us back to square one and leaves us with the question – how do we store the keys?
The Solution is Secure Key Management!
The Silicon Labs’ Secure Engine (SE) is a security subsystem that enables secure key management such as the Long-Term Key (LTK) and the Identity Resolving Keys (IRKs). Secure Engine uses the concept of a Physically Unclonable Function or a PUF to overcome the challenge of securely storing keys.
Physically Unclonable Function (PUF)
First, let us understand what a PUF is. A PUF is a physical structure embedded in an integrated circuit (IC) that is very hard to clone due to its unique micro- or nano-scale properties originating from inherent deep-submicron manufacturing process variations. The static random access memory (SRAM) PUF is the best-known PUF based on available standard components. An SRAM memory cell consists of two cross-coupled inverters and two additional transistors for external connection, hence six transistors in total. When a voltage is applied to each memory cell, it will initialize in a unique 1 or 0 preference state determined by the threshold voltages of the transistors that make up the two cross-coupled inverters. If an SRAM memory array is large enough (1000 to 2000 cells typically), then that random pattern of 1’s and 0’s will represent a statistically guaranteed “unique” fingerprint for that piece of silicon. This unique digital fingerprint is then used to create a symmetric root key called the Key Encryption Key (KEK), which encrypts the keys that need secure storage. Because the device creates its own KEK, you are eliminating the opportunity of the KEK being compromised for malicious intent.
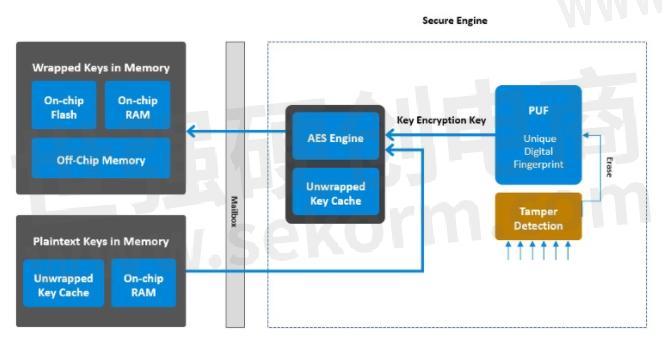
Figure - Secure Key Management
How Silicon Labs Implements Next-Generation Secure Key Storage
1. No Key Encryption Key available to extract!
Silicon Labs’ EFR32BG21 has state-of-the-art secure engine implementation with PUF and Tamper detection. Bluetooth devices are primarily concerned with the secure storage of the LTK and IRKs. In the Secure Vault high parts, the Key Encryption Key generated through the PUF is sent to the symmetric Advanced Encryption Standard (AES) encryption algorithm via a secret bus that cannot even be read by the Secure Engine. The AES Algorithm is then used to encrypt the LTK and IRKs with a standardized key wrapping algorithm and then are sent to either an on-chip flash, an on-chip memory, or an off-chip memory for secure storage in a “wrapped” format. The PUF digital fingerprint and the KEK are re-generated every time the chip is powered up and are only temporarily stored in the Secure Engine RAM. This means the KEK is never left in persistent memory when the chip is powered down, so no secure storage is necessary for the KEK.
2. Tamper Detection
Tamper detection is often overlooked in security suites as the focus is typically on preventing remote attacks. However, tamper detection is a relatively cheap and simple way to avoid local attack vectors from flash reading the keys out of your device. For example, if an unauthorized entity were to try to access the keys with a physical attack, tamper detection can be set up to perform one of the following actions:
• Interrupt the running code
• Reset the chip, or
• Permanently brick the chip.
Selecting the last option would delete the PUF reconstruction data (the digital fingerprint), meaning that there would be no way to ever re-generate the Key Encryption Key, and therefore decrypt any of the already wrapped keys. The encrypted keys will forever remain encrypted. This is an effective nuclear option to ensure that no unauthorized entity can ever access the Bluetooth keys. So, by extension, the Bluetooth devices are secured to the best extent possible.
3. Fault Injection and Side Channel Protection
Silicon Labs Secure Vault High parts all have extensive mitigation against several variations of non-intrusive Differential Power Analysis (DPA) and Electromagnetic Analysis (EMA), which utilize detection and measurement of stray energy emissions from the chip during cryptographic operations and sophisticated statistical analysis to derive private or secret keys. Our crypto algorithms also offer proven protection against Differential Fault Analysis (DFA) and Correlation Power Analysis (CPA). These types of attacks were not all that common in the past as they required a great deal of expertise and money to perform. However, there are tools now available on the open market that do a decent job of these attacks at an affordable price and cook-book ease.
Wrapping it up!
Bluetooth technology will only continue to grow, and with it, so will the need for increased security. Hiding keys in pirate chests and on post-it notes are no longer viable options. Advanced security features like PUF wrapped keys and tamper detection in chips are essential in sensitive industries like medical, high-value asset tracking, access control, etc., where data privacy and identities of devices are crucial requirements. Silicon Labs is at the forefront of meeting these requirements. A testimony to differentiation is that their Bluetooth devices are the first radio SoCs (System on a Chip) to achieve PSA Level 3 certification. Silicon Labs’ Bluetooth devices have also completed extensive independent vulnerability penetration testing from Riscure Security Certification Services as further proof that security features are one of, if not the best in the industry. The secure storage of Bluetooth keys is left to the discretion of device manufacturers in the Bluetooth Specifications. Through Silicon Labs’ security implementation, you can be assured that your Bluetooth devices are as secure as they can be.
- +1 Like
- Add to Favorites
Recommend
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.










































































































































































































































































































































































































































































































































































































































































































































































































































































































































