AI-Based Security at the Endpoint——Renesas‘ RA MCUs Leverage AI to identify and prevent cyber threats

The Internet of Things (IoT) has tRAnsformed the fabric of the world into a smarter and more responsive one by merging the digital and physical universes into one. Over the past few years, the IoT has exhibited exponential growth across a wide range of applications. According to a McKinsey study, the IoT will have an economic impact of $4 - $11 trillion by 2025. The edge continues to become more intelligent, and vendors are racing to support more connected and smart endpoint devices.
Combining high-performance IoT devices with ML capabilities has unlocked new use cases and applications that have resulted in the phenomenon identified as Artificial Intelligence of Things. The possibilities of AIoT — AI at the edge — are endless.
AIoT has the capability to automate the system of processing data and converting IoT raw data into meaningful information. It provides manufacturing sections with the ability to improve production processes by increasing efficiency, product quality, and smoother processes. AI-based industrial applications include maintenance, predictive quality control, fault detection, inventory management, and production planning and optimization.
The AIoT market is forecast to experience a significant Annual Growth Rate (CAGR) of 39.1% by 2026. Other market reports estimate that the AIoT market will reach more than 100$ billion by 2026. According to the Industrial AI and AIoT Market Report 2021–2026, the AI adoption rate in industrial settings has increased significantly from 19% to 31% in about two years. The global market for IoT data as service solutions will further reach $8.89B USD by 2026. These estimations identify the edge devices market as the fastest growing within the AIoT.
With this ever-increasing usage of AI, the need to secure IoT data has become a top-most priority.
Securing the Endpoint
The endpoint in any network is the term that describes any device that is physically at the end of any point in the network. Devices at the endpoint can collect data, analyze, perform computations, and take decisions based on results. Applying AI at the endpoint has its pros, the main one being real-time processing, which provides the needed response with no network transmission delay time.
Security is the biggest challenge confronting the Internet of Things and an impediment to its expansion. The major concern in the security field is that hackers will find new ways of exploiting the vulnerabilities and cause damage or steal information from connected devices. Endpoint security is a part of the overall cybersecurity solution. It protects the endpoint devices from cyberattacks. It is noteworthy that not all attacks on a company occur from an external source. The attackers can be insiders as well with malicious intent, who have access to your network and are able to steal information or infect your network with malware. Security risks can lead to huge financial losses for companies and even governments, as the impact of an attack on IoT is greater than those on traditional networks.
The IoT presents the scalability challenge which means the size of the system is expanding by adding more endpoint devices, and a large number of additional connected devices can be available in a very short time. Endpoint devices are weak points because they are the entry point of any upcoming security threats. As the different types of endpoints have evolved and expanded, the security solutions that protect them have also had to adapt.
One of the main problems in IoT security is that these devices are not only the weakest link in the cybersecurity chain, but they also offer a way for attackers to bypass perimeter defenses. This increases the need for organizations that benefit from IoT technologies to discover new ways of securing IoT devices from exploitation by hackers.
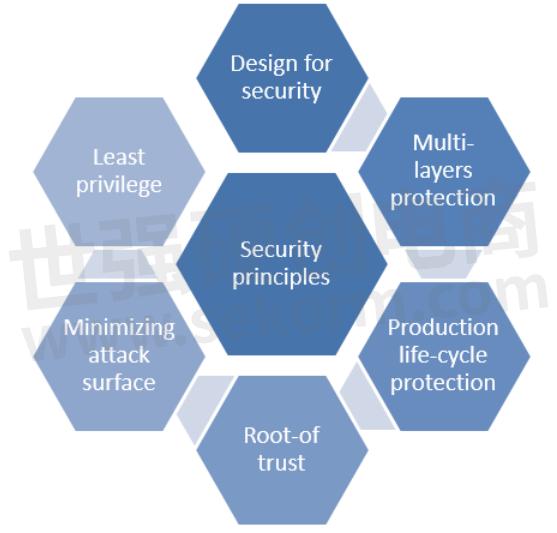
Designing in security needs to be considered from the beginning at the architectural stage. Some of the key security principles include:
1. Least privilege
This is the first basic principle that focuses on ensuring that users have only limited access that allows them to carry out their job.
2. Design for security
There are many processes for embedded systems design which include establishing threat analysis, security requirements, secure design, implementation, test/verification for security, and a response plan in case a problem arises after releasing the product.
3. Multi-layers protection
To provide the systems with guaranteed protection and prevent different types of attacks, it is preferred to apply for the protection in multiple layers through multi-layered platforms.
4. Production life-cycle protection
Besides layers and design for security, protection can be provided during the product lifecycle. This type can guarantee both security and integrity for the product starting from production to shipment, to deployment, and ultimately to their end of life.
5. Root-of trust (RoTs) on the hardware level
RoTs are the basic step to ensure the assurance of the trustworthiness of a device. RoTs are the core of security that is built of hardware, firmware, and/or software that provide a set of trusted, security-critical functions.
6. Minimizing attack surface area
This principle is about removing parts of a system to make it more secure. Minimizing attack surface area questions whether a feature is necessary or not. Now and then redesigning a feature to make it simpler will improve the overall system in the end.
Leverage AI to identify and prevent cyber threats
AI can automate actions based on specific rules, detect threats, improve response times, identify determining patterns, and analyze data at the endpoints. In a recent report from TechRepublic, an organization of medium size can be confronted with more than 200,000 cyber alerts daily. While it may be impossible to deal with the vast number of humans involved, it can be managed by AI.
Every AI cybersecurity solution works in a unique way, and these models become smarter over time. AI uses machine learning and deep learning techniques to assess the behavior of network components over time. It can identify reliable and suspicious patterns and categorize them accordingly. One of AI’s biggest advantages in cybersecurity is the ability to analyze massive amounts of data in a very short time and that too with high performance and low error rate, which is impossible to be done manually.
IoT devices connected to the internet are not as secure as they should be, making them a new frontier for hackers. Therefore, companies ought to explore ways to discover, predict, justify, act, and learn to ensure the protection of their customer's security and privacy.
Security is the foundation for realizing connected AIOT applications across any segment. As the number of connected devices increases, the level of security for embedded devices must also be enhanced. Renesas offers a wide range of security software solutions and products based on the Root of Trust concept that contributes to easier integration of systems and robust security for embedded devices.
Renesas RA MCUs offer customers the ultimate IoT security by combining our secure crypto engine IP with NIST CAVP [Cryptographic Algorithm Validation Program] certifications on top of Arm TrustZone® for Armv8-M, while also providing tamper detection and reinforcing resistance to side-channel attacks.

The RA MCU family is certified to PSA (Platform Security Architecture) Level 2 and offers Security Evaluation Standard for IoT Platforms (SESIP) certifications. The RA family includes solid, hardware-based security features, including integrated crypto subsystems based within the MCU. Renesas' Secure Crypto Engine, an isolated subsystem of the MCU, provides symmetric and asymmetric encryption and decryption, hash functions, true random number generation (TRNG), and advanced key handling (which includes key generation and key wrapping unique to the MCU). In addition, RA MCU integrated SCE (Secure Crypto Engine) access management circuit shuts down the crypto engine if the correct access protocol is not followed, and a dedicated RAM ensures that plaintext keys are never exposed to any CPU or peripheral bus. All these features are well integrated within our FSP (Flexible Software Package) which provides integrated, easy-to-configure support and a collection of Application Projects that enables you to incorporate security into your design effortlessly.
Endpoints are considered an entrance to an IoT system, making them an attractive target for hackers. Hence, it is imperative that designers employ security as a foundation by leveraging loT ready compute devices and relevant deep learning techniques to achieve complete end-to-end security. At Renesas Electronics, we invite you to take advantage of our high-performance MCUs and A&P portfolio combined with a complete SW platform and tools, to build highly secure endpoint applications with added intelligence.
- +1 Like
- Add to Favorites
Recommend
- Renesas Extends RA MCU Family with RA6T1 MCU Group for Motor Control and AI-based Endpoint Predictive Maintenance
- Renesas and Cyberon Partner to Deliver Integrated Voice User Interface Solutions for Renesas RA MCUs Supporting Over 40 Global Languages
- Renesas Extends IoT Security Leadership With PSA Certified Level 2 and SESIP Certification for RA Family MCUs
- Renesas Extends Support for Microsoft Azure RTOS Across 32-bit MCU Families with Simple Licensing
- Renesas Expands RA MCU Family with New RA4 Entry-Line Group Offering Optimal Value with Balanced Low Power Performance and Feature Integration
- Renesas DSP Solution on Renesas Lab on the Cloud, Input Analog Signals Directly From A Signal Generator To The Rx231 Microcontroller Evaluation Board
- Renesas Extends Functional Safety Leadership with SIL3 Certified Solutions for ARM® Cortex®-M23 and -M33-based RA MCUs
- Silicon Labs Expands MCU Platform with a 50MHz Core Frequency New BB5 8-bit MCU Family
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.





























































































































































































































































































































































































































































































































































































































































































































































































































































































