Achieving A Root of Trust With Secure Boot in Automotive RH850 and R-Car Devices




Thank you for taking the time to read our security blog. This is part three in a three-part series about secure boot. If you haven’t check out the previous two articles they are: (Part 1 – Secure Boot Introduction) and (Part 2 – Secure Boot of MCU Devices). In our last installment, my colleague Mr. Yamanaka-san described secure boot on our RH850 MCU devices. In this blog I will cover secure boot on our Arm based Renesas R-Car Gen 3 SoC devices.
Secure boot on R-Car
System on chip (SoC) devices have more complex boot sequences than typical microcontroller devices. Secure boot ensures integrity and authenticity through the entire boot chain. The software can be optionally stored encrypted at rest to protect confidentiality.
Building a chain of trust
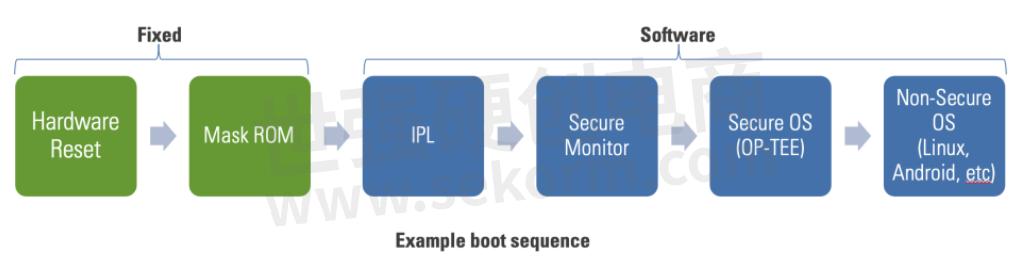
To provide secure boot on R-Car, Renesas builds a chain of trust rooted in the hardware. The mask ROM and HBK (boot key hash) act as an immutable trust anchor. These cannot be altered in production. Throughout the boot chain, each part of the chain of trust is verified by the earlier (authorized) part. Chaining of elements allows all stages verification to point back to the original root of trust, like links in a chain. The starting point of this verification process is the mask ROM of the R-Car. It is executed immediately after reset.
Key Takeaway: Renesas builds a chain of trust rooted in the hardware
·Mask ROM and HBK function as an immutable trust anchor, these cannot be altered
·Each part of the chain of trust is verified by the previous (authorized) part
·The starting point of this verification process is the mask ROM of the R-Car device as the “Root of Trust”
Preparing the secure boot environment
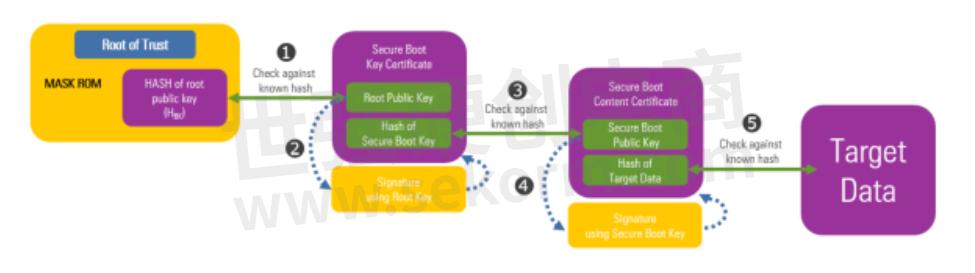
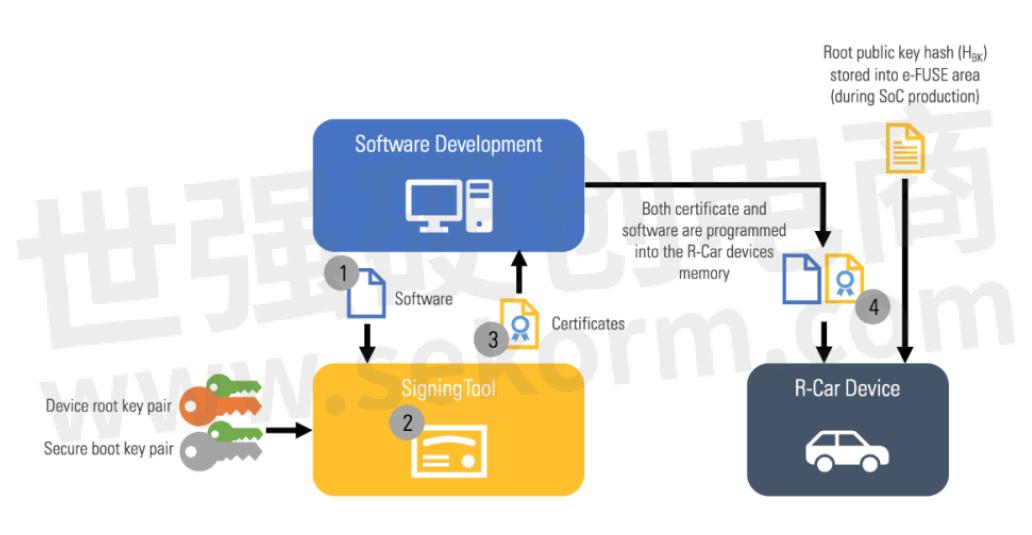
In R-Car devices, secure boot starts with preparing the signing chain. Preconditions to the signing process include generating two RSA key pairs (the device root key pair and the secure boot key pair) and generating the device root public key hash (HBK). Each customer will have a unique root key controlled in their secure OT environment. Root and secure boot private keys must be stored securely to ensure overall system security. Once the key pairs are created, a Renesas supplied tool generates a cryptographic hash of the root public key. This public root key hash (HBK) is provided to Renesas and programed into R-Car devices during manufacturing. The HBK is used in the secure boot chain to verify the integrity and authenticity of the root public key.
Signing images
After the environment is prepared, the signing process can begin. Taking the root and secure boot key pairs and software image as inputs, the signing tool generates two certificates: 1) A root key certificate that contains the public root key and 2) The content certificate that contains the secure boot public key and image signature contents. The software image and certificates are programmed into the R-Car device memory. Only public keys are stored on the R-Car device.
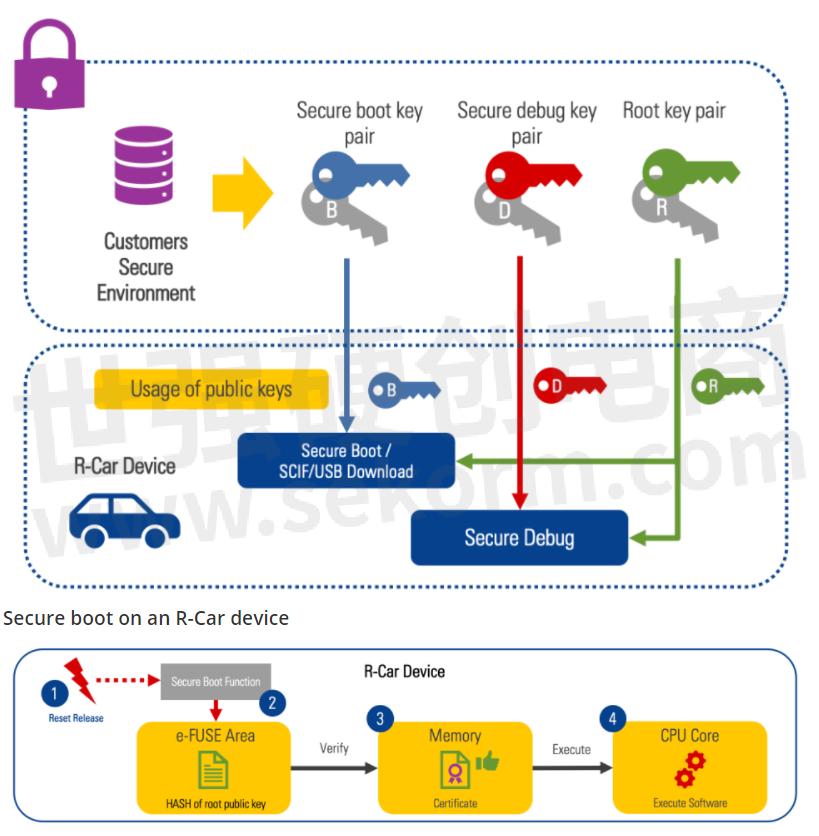
After reset release (1) the Secure Boot function is called (2). The Secure Boot function verifies the software using the root key and content certificates (3). The deployed software will only be executed by the device if the verification process is successful (4).
Here is an exploded version of the secure boot sequence.

Steps:
1.Device reset released
2.The device executes the mask ROM. If device is in security enabled state, secure boot is executed.
3.The mask ROM loads certificates and content from external flash
4.The mask ROM parses the root key certificate and extracts the root key. The root key hash is calculated and compared to the known root key hash (HBK). If the key is correct, the system proceeds to the next step.
5.The mask ROM calculates and compares the hash of the boot key found in the secure boot content certificate to the secure boot key hash found in the key certificate (verified in the previous step). If the check passes, the public key is used to verify the content certificate signature. If the in the content certificate is valid, the data in the content certificate is used to calculate the validity and integrity of the next boot stage. If everything check out execution jumps to the next boot stage.
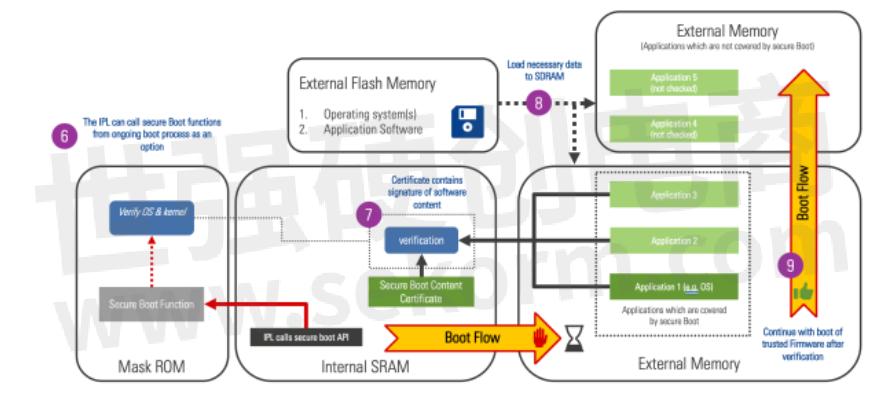
6.Subsequent boot stages can call into the mask ROM secure boot functions to validate later stage content. In this example the IPL calls into the mask ROM API to verify applications 1-3. By calling the mask ROM API in later stages, the designer can take advantage of the hardware acceleration for the RSA signature check and SHA accelerator for hashing.
7.The mask ROM verifies the content certificate is loads the next boot stage
8.The IPL can validate every image, or only a subset of images it loads. In this example application 1-3 use the secure boot API which application 4 and 5 use another method.
9.When the IPL is done loading and verifying content, it jumps to the next boot stage.
Conclusion:
SoCs have a longer boot chain than MCU devices. The secure boot logic in our R-Car devices allows the designer to take advantage of hardware acceleration of signature checks throughout the boot process. Renesas R-Car devices leverage hardware as the secure root of trust for building dependable, secure systems. Thank you for taking the time to learn more about secure boot on R-Car devices!
- +1 Like
- Add to Favorites
This document is provided by Sekorm Platform for VIP exclusive service. The copyright is owned by Sekorm. Without authorization, any medias, websites or individual are not allowed to reprint. When authorizing the reprint, the link of www.sekorm.com must be indicated.
Recommend
Renesas Introduces How Secure Boot Is Realized on Both Types of Devices
2021-12-30 - Design Article Renesas this blog article, part 2 in a three-part series, aims to give readers a basic understanding of what secure boot is and why it is needed.
Considerations in Wi-Fi 6 AP Design
2022-11-06 - Design Article In this blog, we will cover considerations helpful to those of you who are presently operating or deploying service with Wi-Fi 5, or an older generation of Wi-Fi and are looking to move forward to Wi-Fi 6.
Radar transceivers: a key component for ADAS & Autonomous Driving-Basics of FMCW radar
2021-10-26 - Design Article This entry has provided an overview of the operating principle of the FMCW radar, used in automotive applications, and its implementation using MMICs and MCU/SoC.
MCU/SOC products announcement of Full Carton Product Change Notice (SAG-B-22-0002)
11/30/2022 - PCN/EOL
片上系统,SOC,MCU,单片机,R4F20102NFA#U1,R4F20102NFA#U0,UPD78F0537AGB-GAH-M1-AX,DF71494AD80FPV,UPD78F1168AGC(S)-UEU-M1-AX,R5F56108WNBG#U0,DF71324AD80FPV,UPD78F0501AMCA-CAB-Q-G,R5F56108VDFP#H0,R7FA6M5AG2CBG#AC0,R5F562TADDFF#V3,UPD70F3613M2GBA-GAH-AX,R7FA4M2AC3CNE#BA0,R7FA4M2AB3CFP#BA0,R5F72165ADFP#H1,R5F562TADDA26FP#V1,R5F562N8BDFP#H0,UPD78F1503AGC-UEU-M1-AX,R7FS7G27G3A01CFP#BA0,UPD78F0525AGB(S)-GAG-AX,UPD70F3614M2GBA-GAH-AX,UPD78F1156AGK(S)-302-GAK-M1-AX,UPD78F1166AGF(R)-GAS-M1-AX,UPD720211K8-711-BAL-A,R5F5610GVNFP#H0,R5F72531MKFPU#HZ,R7FA6M5BG3CFB#AA0,R5F72165BDFP#V1,R7FA2E1A73CFM#BA0,UPD703500GM-GAR-M1-AX,R5F3650ECDFB#10,UPD70F3913GC(R)-UEU-AX,R7FA6M4AE3CFB#AA0,DF71464AD80FPV,R5F74974D100FP#G0,R7FA6E10D2CNE#BA0,UPD78F0452GK(S)-GAJ-AX,V850ES/J,R5F562TADDA41FP#H1,R5F72395BDFP#H0,UPD70F3333GC(A)-8EA-A,V850ES/H,UPD78F0455GK(S)-GAJ-AX,R5F56318CDBG#U0,V850ES/F,R5F563TEADFA#V0,V850ES/S,R5F21334DNFP#30,R5F562GAADFH#H1,R5F5630DCDBG#G0,UPD760191GC-355-8EA-M1-A,UPD760191GC-358-8EA-A,F71252DA26FPV#G1,R5F562T6AGFM#H3,UPD70F3939BGJA-GAE-M1-G,UPD70F3371M1GBA2-GAH-AX,R7FA4M2AD3CFL#BA0,R5F563TEADFA#V1,R7FA2L1AB2100DFM#BA0,UPD703111BGM-15-UEU-A,R5F72167BDFP#H1,R7FA6T1AB3CFM#AA0,R7FS3A6783A01CNE#AA0,R7FA2L1AB2DFL#BA0,R7FA6M5BH2CBG#AC0,UPD70F3796F1(R)-023-CAH-A,R5F2135ACNFP#30,UPD70F3515F1(R)-HN6-A,R7FA6M4AE3CFP#AA0,R5F72543RDKBGV,R7FA6M1AD3CFP#BA0,UPD70F4012AM1GDA-FAD-M1-AX,UPD760191GC-329-8EA-A,R5F56218BDFP#H0,R7FA6M1AD3CFP#BA5,UPD68225GK-011-GAK-KW-AX,R7FA4M2AC3CFM#AA0,R5F56318DGFP#V0,R5F21336TNFP#30,R5F563TEEDFA#H0,R5F563NFDGFB#V0,R4F2463VTE34DV,R5F36406CDFB#10,R7FA2E1A53CFL#AA0,UPD78F1500AGK(S)-GAK-M1-AX,R5F21334DNFP#10,UPD78F1505AGC-UEU-M1-AX,DM71494BNA77FPV#GZ,R7FS7G27G3A01CFB#BA0,UPD70F3766GF(R)-M03-GAT-M1-AX,UPD720202K8-711-BAA-M1-A,R5F2135ACNFP#10,UPD70F3914GF(S)-GAS-M1-AX,UPD78F0525AGB(S)-GAG-M1-AX,UPD70F3371M1GBA2-GAH-M1-AX,R7FA6M5BG3CFC#AA0,DF70865AN80FPV,UPD8512GA-GAM-AX,G71242DA17FPV#G1,R5F72167ADFA#H1,R7FA6M5BF3CFC#BA0,UPD70F3570GBA2-GAH-AX,UPD70F3743GJ(R)-GAE-M1-AX,R7FA4E10D2CNE#BA0,R5F51116ADLF#UA,R7FA4E10D2CNE#BA5,R5G72434DA06FP#U0,R5F563T6EGFM#V0,R5F72AYBKFP#H9,R5F563TEDDFB#V0,R5F563TEDDFB#V1,R5F72A28KACFP#VZ,UPD70F3592AM1GMA-GBK-AX,R5F563NBCDBG#G0,UPD70F3766GF(R)-GAT-M1-AX,R5F36406CDFB#30,UPD68228GK(A2)-902-GAK-M1-AX,R7FA6M5BG3CFP#AA0,R7FA4M3AF3CFP#BA0,G71243DA20FPV#Z1,UPD78F0537AGA(R)-HAB-AX,R5F21336TNFP#10,UPD78F1142AGB(S)-GAH-M1-AX,R5F562TADDFH#V1,R5F563TCEDFP#V1,R5F564MFCGFP#H1,R5F562TADDFH#V3,R5F72A26K3DFP#VZ,R7FA2L1A92DFL#BA0,UPD70F3505AGCA1-UEU-AX,R5F72546RDKBGV#GZ,R5F72145BDFA#H1,R4F24256NFAU#HZ,R7FA6M3AF3CFP#BA0,R5F563NBDDBG#U0,DM71494BNA74FPV,R5F51113ADLM#UA,UPD760191GC-308-8EA-A,UPD720202K8-711-BAA-A,R7FA4M3AE3CFM#BA0,UPD70F3451GC(S)-UBT-A,R7FA6M3AF3CFB#BA0,R5F5110JADLM#U0,R7FA4M3AF3CFB#BA0,R7FA4E10B2CNE#AA0,R5F563NECDBG#U0,R7FA2A1AB3CFM#BA0,R7FS3A77C3A01CNB#AA1,R5F51105ADLF#G0,R7FA6M5BG2CBG#BC0,R5F562TADDA42FP#H1,R7FA4E10B2CNE#AA5,R5F21356CNFP#10,R5F56216BDFP#V0,R5F72543RKBGV,R5F562TADDFH#H3,R7FA6M4AD3CFM#AA0,R5F5630ADGFP#H0,DM70844ADA20FPV,R5F21276SNFP#10,UPD78F0502AMCA2-CAB-M1-G,R4F20203RNFD#V0,R7FA2E1A92DFM#BA0,R7FS3A37A3A01CNB#BA0,UPD70F3454F1(R)-DA9-A,R4F20203DFD#U0,R5F562T6DDFF#V1,UPD703111GM-15-UEU-A,UPD70F3383M1GMA-GAR-AX,R7FA6M4AD3CFM#AA5,R5F5631ECDBG#U0,R5F72374ADFP#V0,R5F562T6DDFF#V3,R5F72544RKBGV,R5F72165BDBG#G1,R5F72531KFPU#ZA,R5F364AENFB#30,R7FA4M2AD3CNE#AA5,R5F72A07K7CAFM#VZ,R7FA4M2AC3CFL#AA0,R7FA4M2AD3CNE#AA0,R5F562TADDFH#H1,UPD78F0513AGB(S)-434-GAF-M1-AX,R7FS5D37A3A01CNB#AA0,DF71324AD80FPV#GZ,DF71494AD80FPV#GZ,R5F56108VNFP#V0,R5F563TBADFA#V1,R5F74954BDFA#V1,R7FA6T1AD3CFM#BA0,UPD78F0452GK(S)-GAJ-M1-AX,R5F562TADDA42FP#V1,UPD70F3468GJ(A2)-GAE-M1-AX,R5F21354CNFP#30,R7FS7G27H3A01CFC#AA0,R7FA4M1AB3CNB#BA0,R7FA6M5BF3CFB#BA0,UPD70F3454GC(R)-R01-8EA-A,UPD70F3796F1(R)-023-CAH-M1-A,R5F56104VNFP#H0,R5F72867D100FA#G2,R5F72AW3KFP#V9,R5F563TCDDFA#H0,UPD720115K8-711-BAK-M1-A,R5F563TCDDFA#H1,DF71323AD80FPV#GZ,UPD78F1167AGC(S)-UEU-AX,R7FA2E1A93CFK#BA0,R7FA6M5ZH3CFB#AA0,R5F21265SNFP#10,R5F61668RN50BGV,R5F5631BDDBG#G0,R7FA6E10D2CFM#AA0,R7FA6M2AF3CFB#AA0,R5F364AENFB#10,R5F3650ENFB#30,UPD760191GC-352-8EA-M1-A,R5F72543RKBGV#GZ,R7FA6M1AD3CFM#BA0,UPD78F1500AGK(R)-GAK-AX,R7FA6M1AD3CFM#BA5,R5F72A08KACFM#HZ,UPD70F3454GC(R)-R01-8EA-M1-A,R5F72543RMKBGV#GZ,UPD70F3453GC(R)-018-8EA-A,R7FA2L1AB3CFP#AA0,R5F72A28KADFP#VZ,UPD760191GC-323-8EA-A,R7FA4M3AF3CFM#AA0,R7FA6E10D2CFM#AA5,R5F72531DAKFPU#HZ,R7FA6M5AG3CFP#BA0,UPD720201K8-711-BAC-A,R7FA6M4AF3CFP#BA0,R7FA6M5AH3CFC#BA0,DF71253N50FAV#G1,R7FA2E1A92DFJ#BA0,UPD70F3747GB(R)-GAH-M1-AX,R5F21354CNFP#10,R5F72A28KADFFP#VZ,UPD78F0535AGB-GAH-M1-AX,R7FA4M1AB3CFL#AA0,R7FA6M1AD3CNB#BA0,UPD78F1201MC(S)-CAB-M1-AX,UPD78F1168AGC(S)-UEU-AX,R5F72530ZAKFPU,R7FA6M1AD3CNB#BA5,R5F562T7GDFF#H3,R7FA2E1A92DFL#BA0,R7FA6E10F2CFP#BA5,R4F24259DVFAU,R7FA6E10F2CFP#BA0,R7FA2E1A53CFJ#AA0,R5F72A08KABAFM#VZ,UPD70F3454GC(S)-8EA-M1-A,UPD70F3370AM2GBA-GAH-AX,R5F56318DGFB#H0,R5F5631BCDBG#G0,DF71253N50FPV#Z1,UPD78F1164AGF-GAS-AX,R5F72533KFPU,UPD703500GM-GAR-AX,R5F5631EDDBG#U0,R7FS3A6783A01CNF#AA0,R5F563TEBDFP#V1,UPD70F3537F1A9-
MCU5 RH850 & RL78 AUTOMOTIVE MCU INTRO
2023年9月 - Selection guide
汽车级微控制器(MCU),系统单芯片(SOC),RH850/F1KM-S1,RH850/F1KM-S4,RH850/P1X-C,RH850/C1M-A,E2X,C1X,F1X,RH850/C1M-A2,RH850/F1KH-D8,RH850/P1X,RL78/F22,U2AX,RL78/F23,RH850/F1X,U2BX,RL78/F13,RL78/F24,RL78/F14,RL78/F25,P1X,RL78/F15,RH850,RL78/F1X,RL78
Renesas next generation Automotive Vehicle Computer VC4 – A winning combo solution with R-Car ecosystem partner support
2022-04-20 - New Product Introduction The VC4 is based on a complete Renesas chipset is the ideal platform to evaluate new E/E Architectures using the R-Car S4 in Gateway, Car Server or Zone Control applications.
DA14531 Bluetooth® Direct Test Mode
14-Feb-2023 - Application note & Design Guide
片上系统,超低功耗SOC,BLE SOC,ULTRA-LOW POWER SOC,SOC,BLE SOC语言,DA14531
Solutions for XILINX® FPGAs & SoCs
August 2021 - Technical Documentation
时钟发生器/缓冲器,稳压器,数字电源管理,抖动衰减器,时钟和定时产品,序列器/监控器,精密电压参考,电源解决方案
Renesas R-Car SoC and RH850 MCU to be Used in Honda SENSING System
2022-03-05 - Manufacturer News Renesas Electronics Corporation announced the expansion of its collaboration with Honda in the field of advanced driver-assistance systems (ADAS).
Pairing An R-Car SoC Microprocessor with RH850 and PMIC, System Solution for CoGW ECUs Can Be Realized
2021-01-31 - Application solution Article Our dedicated, system solution for CoGW ECUs can be realized by pairing an R-Car system-on-a-chip (SoC) microprocessor with an RH850 microcontroller (MCU) and various analog chips such as the Power Management Integrated Circuit (PMIC).
How to Build Together a Safe and Efficient AD & ADAS Central Computing Solution
2023-11-30 - Technical Discussion Should RENESAS stop here and call it a success? Clearly no! Progress has no limits and by working together we ensure to constantly update our understanding of how autonomous systems of tomorrow will be and anticipate that by providing state-of-the-art processing solutions that would bring them successfully to the mass market.
DA1469x Multi-Core Bluetooth®5.2 SoC Family with System PMU Datasheet
22-Apr-2022 - Datasheet
MULTI-CORE WIRELESS MICROCONTROLLERS,多核蓝牙®5.2 SOC,多核无线微控制器,MULTI-CORE BLUETOOTH®5.2 SOC,DA14691-00000HQ2,DA1469X-RRXXXYYZ,DA14697-00000HR2,DA14691,DA1469X,DA14697,DA14695-00000HQ2,DA14699,DA14699-00000HR2,DA14695
Renesas and FAW Establish Joint Laboratory to Accelerate Development of Next-Generation Smart Vehicles
2021-01-08 - Manufacturer News Renesas a premier supplier of advanced semiconductor solutions, and China FAW Group Corporation (FAW), a leading automotive maker in China, announced the establishment of a joint laboratory in Changchun, China, effective December 1, 2020.
SLG7RN46137 GreenPAK ™ CN363 Smart Power on/off Sequence Controller
12/12/2022 - Datasheet
片上系统,SMART POWER ON/OFF SEQUENCE CONTROLLER,SOC,智能电源开/关顺序控制器,SLG7RN46137,SLG7RN46137V,SLG7RN46137VTR
DA16200 Ultra Low Power Wi-Fi SoC Data Sheet
17-Jan-2022 - Datasheet
片上系统,超低功耗WI-FI SOC,SOC,ULTRA LOW POWER WI-FI SOC,DA16200-00000F22,DA16200-00001F22,DA16200-00001A32,DA16200-RRXXXYYZ,DA16200,DA16200-00000A32
More Version(s)Electronic Mall
Integrated Circuits
Discrete Components
Connectors & Structural Components
Assembly UnitModules & Accessories
Power Supplies & Power Modules
Electronic Materials
Instrumentation & Test Kit
Electrical Tools & Materials
Mechatronics
Processing & Customization












































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































